In the aftermath of a malware attack, the Windows Defender Security settings page may show the message Some settings are managed by your organization or This setting is managed by your administrator. The real-time protection and cloud-based protection options may remain disabled or grayed out.
Here is what the Windows Defender Settings page might look like. The controls for real-time protection, cloud-based protection, and Automatic sample submission options may be disabled and locked down or grayed out.
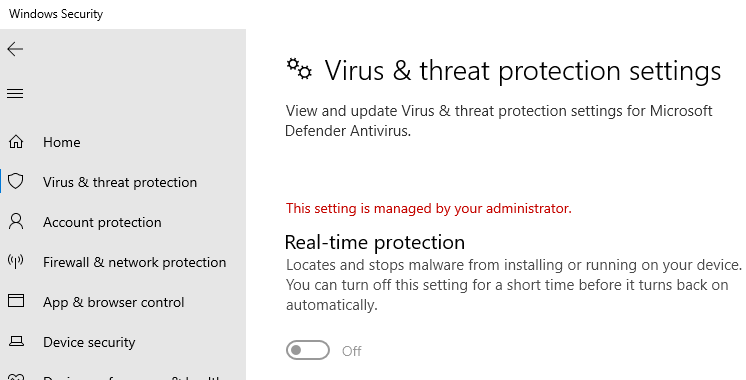
If you’ve installed a 3rd party anti-virus, Windows Defender gets disabled automatically. It’s normal. In that case, you’ll see the message “You’re using other antivirus providers.” instead.
If Microsoft Defender group policies or registry-based policy settings are in effect, the following error appears when opening the Security at a glance page:
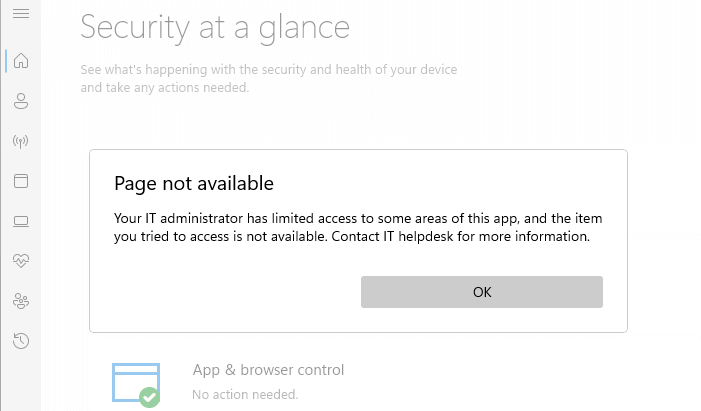
Page not available Your IT administrator has limited access to some areas of this app, and the item you tried to access is not available. Contact IT helpdesk for more information.
Virus & Threat Protection is Missing?
In some situations, the Virus & threat protection section may be missing. The Virus & threat protection section in the Windows Security user interface lets you configure every aspect of the Microsoft Defender Antivirus — such as real-time protection, tamper protection, ransomware protection, Controlled folder access, and other important settings.
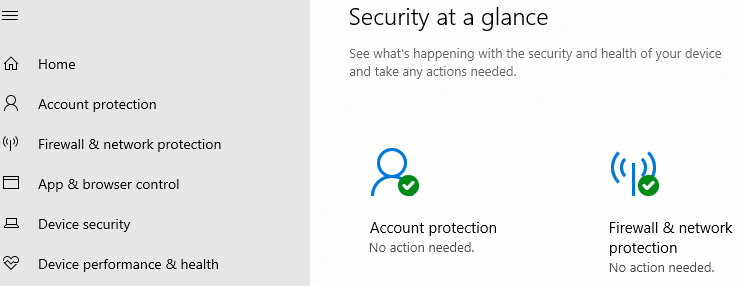
Malware and viruses may add registry entries that hide the Virus & threat protection section from the user interface. This is caused by some registry-based Policy settings. (Jump to this part.)
This post tells you how to activate Microsoft Defender real-time protection and other settings by removing the entire Microsoft Defender Antivirus registry-based policies previously added by malware, a 3rd party tweaker, or a privacy protection tool. The “Virus & Threat Protection” section should also be restored automatically after removing all the Policies.
Cause
Third-party privacy protection tools
If you have used third-party anti-spy tools such as O&O ShutUp, make sure you reset all “Windows Defender and Microsoft SpyNet” settings in that program.
Connected to Domain/Azure AD?
If you’ve connected your computer to a domain or work/school account, please contact your IT administrator or disconnect the system from the work/school account.
Or disconnect from your Work/School/Azure AD by opening Settings → Accounts → Access work or school and click on your Azure AD account, and click Disconnect.
Malware?
Malware can add registry entries that disable the real-time monitoring capabilities of Windows Defender, and also hide certain parts of the Windows Defender user interface from users.
First, make sure you eliminate malware with help from an expert or friend — given the complexity of the malware infestation, professional help may be suggested. You may also try Windows Defender Offline. in addition.
The malware removal procedure is complex and is beyond the scope of this article. After eradicating the malware, remove the registry-based policy settings added by malware.
Virus and Threat Protection missing?
If the Virus & threat protection section is missing in the Defender user interface, it may be caused by one of the following group policy settings:
Enable the headless UI modegroup policy setting (Registry value:UILockdown)Hide the virus and threat protection areagroup policy (Registry value:UILockdown)- A registry-based policy — value named
AllowUserUIAccess.

The following are the registry values that hide the Virus & threat protection category in the Windows Defender Security user interface.
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\UX Configuration] Value: UILockdown [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender Security Center\Virus and threat protection] Value: UILockdown [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager] Value: AllowUserUIAccess
Clearing the above policies especially should reinstate the Virus & threat protection option back. The “defender-policies-remove.reg” registry file below removes all the Microsoft Defender Policies and restores the Virus & threat protection section as well.
Remove All the Microsoft Defender Policies
Option 1: Remove Microsoft Defender Registry-based Policies
gpedit.msc) on the local computer, you need to follow “Method 2” to remove the Policies.Automate the following registry modifications using defender-policies-remove.reg (zipped). Unzip and run the enclosed REG file. After running it, you may want to open the Registry Editor to ensure the “Windows Defender” Policies key doesn’t exist. Once done, restart Windows for the changes to take effect. If you’re unable to apply the above registry file, launch Windows in Safe Mode and try merging the file again.
To manually remove Microsoft Defender Antivirus policies using Regedit:
- Start the Registry Editor (regedit.exe) and go to the following branch:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender
- Export the branch to a .reg file.
- Right-click “Windows Defender” and choose Delete.
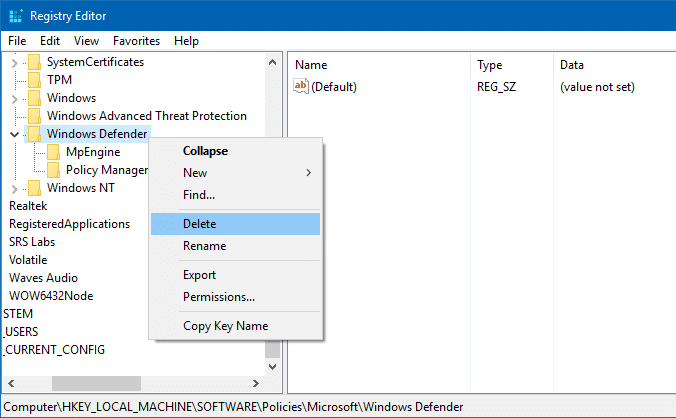
Windows Defender Policy keys in the registry. - Similarly, backup the following branch (if exists) to a .reg file:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection
- Delete the “Windows Advanced Threat Protection” key.
- Next, backup the following branch (if exists) to a .reg file:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender Security Center
- Delete the “Windows Defender Security Center” key.
- Exit the Registry Editor.
- Restart Windows.
Note that this completely clears the policy settings for Microsoft Defender Antivirus and Windows Security page. By default, in a clean installation of Windows, no policies are set for Defender.
After removing all the policies, you may want to enable PUA or adware protection in Windows Defender. If you had already enabled the setting before, you’d need to redo the procedure now.
Option 2: Remove Windows Defender Policies using Group Policy Editor
If you have previously enabled Defender Policies using gpedit.msc (Windows 10/11 Professional or higher editions), you’ll need to use the same tool to remove the policies. The relevant Microsoft Defender Antivirus Group Policies are available in the following branch of the Group Policy Editor (gpedit.msc).
Computer Configuration → Administrative Templates → Windows Components → Microsoft Defender Antivirus Computer Configuration → Administrative Templates → Windows Components → Windows Security
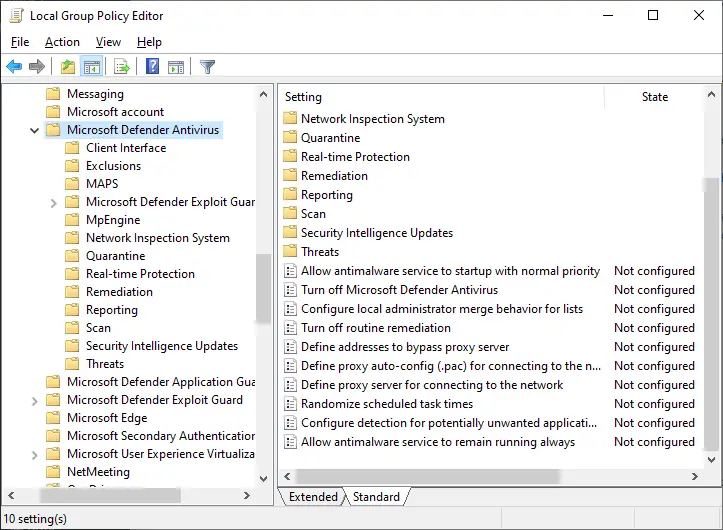
Note that in earlier versions of Windows 10, the policy settings would be located under “Windows Defender” instead of “Microsoft Defender Antivirus”.
There are 100+ policy settings in Windows 10/11, with the items in every sub-branch put together.
Running the Resultant Set of Policy utility (Rsop.msc) or gpresult /h <path>\gpreport.html command shows you which policies are currently enabled.
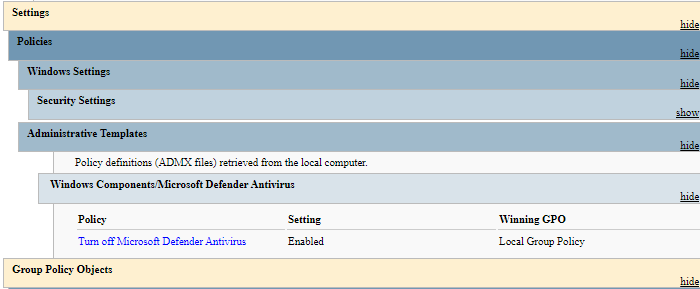
You need to make sure they’re set to “Not configured.”
Microsoft Defender Antivirus
Allow antimalware service to startup with normal priority Turn off Microsoft Defender Antivirus Configure local administrator merge behavior for lists Turn off routine remediation Control whether or not exclusions are visible to Local Admins Define addresses to bypass proxy server Define proxy auto-config (.pac) for connecting to the network Define proxy server for connecting to the network Randomize scheduled task times Configure detection for potentially unwanted applications Allow antimalware service to remain running always
Also, check the following sub-branches in the above location, and set each policy setting to “Not configured.”
Microsoft Defender Antivirus\Client Interface
Display additional text to clients when they need to perform an action Suppress all notifications Suppresses reboot notifications Enable headless UI mode
Microsoft Defender Antivirus\Device Control
Define device control policy groups Define device control policy rules
Microsoft Defender Antivirus\Exclusions
Turn off Auto Exclusions Extension Exclusions Path Exclusions Process Exclusions
Microsoft Defender Antivirus\MAPS
Configure the 'Block at First Sight' feature Join Microsoft MAPS Configure local setting override for reporting to Microsoft MAPS Send file samples when further analysis is required
Microsoft Defender Exploit Guard\Attack Surface Reduction
Exclude files and paths from Attack Surface Reduction Rules Configure Attack Surface Reduction rules
Microsoft Defender Exploit Guard\Controlled Folder Access
Configure allowed applications Configure Controlled folder access Configure protected folders
Microsoft Defender Exploit Guard\Network Protection
Prevent users and apps from accessing dangerous websites
Microsoft Defender Antivirus\MpEngine
Enable file hash computation feature Configure extended cloud check Select cloud protection level
Microsoft Defender Antivirus\Network Inspection System
Turn on definition retirement Specify additional definition sets for network traffic inspection Turn on protocol recognition
Microsoft Defender Antivirus\Quarantine
Configure local setting override for the removal of items from Quarantine folder Configure removal of items from Quarantine folder
Microsoft Defender Antivirus\Real-time Protection
Turn off real-time protection Turn on behavior monitoring Scan all downloaded files and attachments Monitor file and program activity on your computer Turn on raw volume write notifications Turn on process scanning whenever real-time protection is enabled Define the maximum size of downloaded files and attachments to be scanned Configure local setting override for turn on behavior monitoring Configure local setting override for scanning all downloaded files and attachments Configure local setting override for monitoring file and program activity on your computer Configure local setting override to turn on real-time protection Configure local setting override for monitoring for incoming and outgoing file activity Configure monitoring for incoming and outgoing file and program activity
Microsoft Defender Antivirus\Remediation
Configure local setting override for the time of day to run a scheduled full scan to complete remediation Specify the day of the week to run a scheduled full scan to complete remediation Specify the time of day to run a scheduled full scan to complete remediation
Microsoft Defender Antivirus\Reporting
Configure time out for detections requiring additional action Configure time out for detections in critically failed state Turn off enhanced notifications Configure Watson events Configure time out for detections in non-critical failed state Configure time out for detections in recently remediated state Configure Windows software trace preprocessor components Configure WPP tracing level
Microsoft Defender Antivirus\Scan
Check for the latest virus and spyware security intellgence before running a scheduled scan Allow users to pause scan Specify the maximum depth to scan archive files Specify the maximum size of archive files to be scanned Specify the maximum percentage of CPU utilization during a scan Scan archive files Turn on catch-up full scan Turn on catch-up quick scan Turn on e-mail scanning Turn on heuristics Scan packed executables Scan removable drives Turn on reparse point scanning Create a system restore point Run full scan on mapped network drives Scan network files Configure local setting override for maximum percentage of CPU utilization Configure local setting override for the scan type to use for a scheduled scan Configure local setting override for schedule scan day Configure local setting override for scheduled quick scan time Configure local setting override for scheduled scan time Configure low CPU priority for scheduled scans Define the number of days after which a catch-up scan is forced Turn on removal of items from scan history folder Specify the interval to run quick scans per day Start the scheduled scan only when computer is on but not in use Specify the scan type to use for a scheduled scan Specify the day of the week to run a scheduled scan Specify the time for a daily quick scan Specify the time of day to run a scheduled scan
Microsoft Defender Antivirus\Security Intelligence Updates
Define the number of days before spyware security intelligence is considered out of date Define the number of days before virus security intelligence is considered out of date Define file shares for downloading security intelligence updates Turn on scan after security intelligence update Allow security intelligence updates when running on battery power Initiate security intelligence update on startup Define the order of sources for downloading security intelligence updates Allow security intelligence updates from Microsoft Update Allow real-time security intelligence updates based on reports to Microsoft MAPS Specify the day of the week to check for security intelligence updates Specify the time to check for security intelligence updates Define security intelligence location for VDI clients Allow notifications to disable security intelligence based reports to Microsoft MAPS Define the number of days after which a catch-up security intelligence update is required Specify the interval to check for security intelligence updates Check for the latest virus and spyware security intelligence on startup
Microsoft Defender Antivirus\Threats
Specify threats upon which default action should not be taken when detected Specify threat alert levels at which default action should not be taken when detected
Windows Components\Windows Security\Account Protection
Hide the Account protection area
Windows Components\Windows Security\App and browser protection
Prevent users from modifying settings Hide the App and browser protection area
Windows Components\Windows Security\Device performance and health
Hide the Device performance and health area
Windows Components\Windows Security\Device performance and health
Disable the Clear TPM button Hide the TPM Firmware Update recommendation Hide the Secure boot area Hide the Security processor (TPM) troubleshooter page Hide the Device security area
Windows Components\Windows Security\Enterprise Customization
Specify contact company name Specify contact email address or Email ID Configure customized notifications Configure customized contact information Specify contact phone number or Skype ID Specify contact website
Windows Components\Windows Security\Family options
Hide the Family options area
Windows Components\Windows Security\Firewall and network protection
Hide the Firewall and network protection area
Windows Components\Windows Security\Notifications
Hide non-critical notifications Hide all notifications
Windows Components\Windows Security\Systray
Hide Windows Security systray
Windows Components\Windows Security\Virus and threat protection
Hide the Ransomware data recovery area Hide the Virus and threat protection area
![]() If some of them already read as “Not configured”, set it to “Enable, click Apply and set it back to “Not configured.” This is to clear the registry values successfully.
If some of them already read as “Not configured”, set it to “Enable, click Apply and set it back to “Not configured.” This is to clear the registry values successfully.
Last updated on 17-Aug-2022 for Windows 10 21H2.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!

This is a bug that also shows up in the Windows Update Settings app
@Davin: Are you using Windows Insider Preview build, per chance? It’s a known issue in the latest build.
Thank you so much, this was really helpful.
@Julio: Glad to hear. Thanks for writing.
Great post!
really useful after lot of time spent…
Thx!
Works like a charm for me! Thanks for writing
Thank you so much really helped me out
BIG BIG THANKS.
my Defender can work on scan now.
I Do All Of The Above Although Those branches were not in my registry , and all the policies are set to not configure , still ,all the settings are grated out and security at a glance is empty , and WD not working ,in anyway
@Hamid: Pls check out:
Windows Defender Service Missing; Security at a glance page is Empty:
https://www.winhelponline.com/blog/windows-defender-service-missing-security-page-empty/
Thank you, its working
Lmao. Thank you so much this helps me!( January 19,2019) I just want to ask what is the purpose of the back up? If it will be install automatically by windows?
And also what is the purpose of PUA and adware protection? (PS: I`m not yet enabling it)
Hi, Thnx for the post..It really works..Since you seem like person with good knowledge, can u also help me with 0x80070424 this error? I am getting this when i try to update windows..and in services.msc list windows update option is missing..so I cannot go that route..can u help me with this? plss..
Thanks a lot. I’ve solved using this link https://www.winhelponline.com/blog/wp-content/uploads/2017/01/defender-policies-remove.zip.
Wow thank you so much, my windows defender has started working 🙂
Wow thank you so much, my windows defender has started working 🙂
It’s coming back every day.
amazing… What I do is just go to “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender”
and delete it. as simple as that.
Abrakadabra… Windows Defender Real-time protection in my Windows is on again…
Thanks..so..much…
Thanks for the article. Helped me!
Guys none of these solutions worked for me.
At the end I’ve found that downloading a windows update SOLVE the case.
(I did it although the system was up to date according to windows update)
Go to
https://www.microsoft.com/en-us/software-download/windows10
and download the latest update
men i cant turn/off my real time protection because it saids you’re using other anti virus protection
@Sean:
“If you’ve installed a 3rd party anti-virus, Windows Defender gets disabled automatically. It’s normal. In that case, you’ll see the message “You’re using other antivirus providers.” instead.”