Windows Defender can detect and remove malware and viruses, but it doesn’t catch Potentially Unwanted Programs or crapware by default. However, there is an opt-in feature that you can enable to make Microsoft Defender antivirus scan and eliminate adware, PUAs, or PUPs in real-time.
Potentially Unwanted Program (PUP), Potentially Unwanted Application (PUA), and Potentially Unwanted Software (PUS) refer to the category of software that is considered unwanted, untrusted or undesirable. PUPs include adware, dialers, fake “optimizer” programs, toolbars, and search bars that come bundled with applications.
PUAs don’t fall under the definition of “malware” as they’re not malicious, but still, some PUAs are classified as “risky.”
Bottom line: You don’t need “Potentially Unwanted” stuff in your system regardless of the risk level unless you seriously believe that the benefits offered by a particular program outweigh the risks or inconvenience created by the PUP which accompanied the main program.
GUI option
On Windows 10 2004 (and higher) and Windows 11, Windows Defender scans for PUAs by default. Also, you have the option Potentially unwanted app blocking on the Windows Defender Security settings page. You can enable/disable the option using GUI.
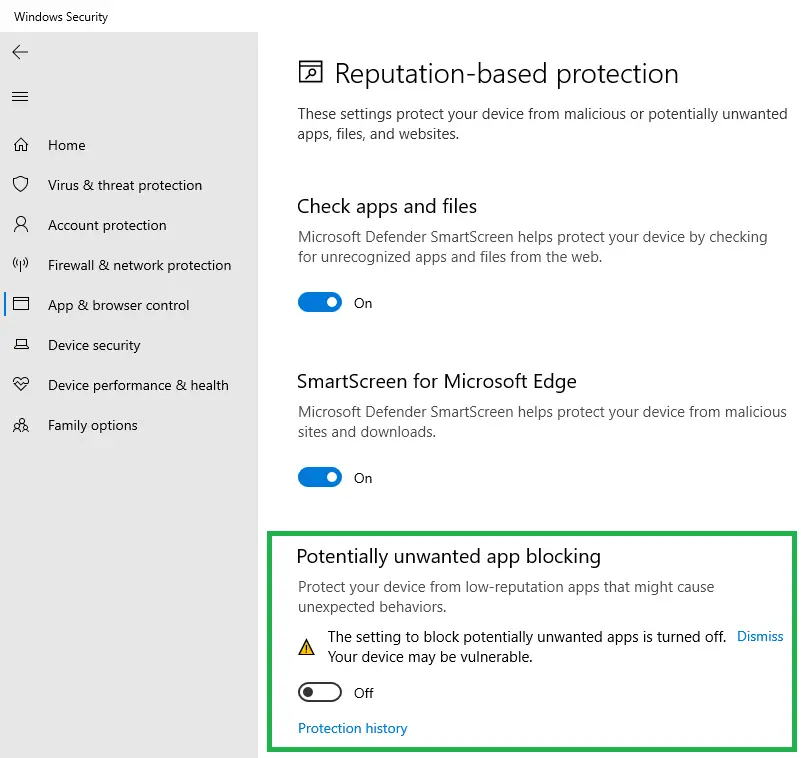
For earlier versions of Windows, follow the procedure below to enable the scanning of PUAs.
Here is how to enable scanning and removal of adware, PUP/PUA using Windows Defender (in Windows 8 and higher).
Enable Windows Defender real-time scanning for PUA/PUP
There are three different ways to enable PUA protection in Windows Defender, but I’m unsure which setting takes precedence in the event of a conflict. The registry location is different in each method described. It’s advisable to use only one of the following methods to avoid confusion.
Method 1: Enable PUA Protection Using PowerShell
Start PowerShell (powershell.exe) as administrator.
Run the following command and press ENTER:
Set-MpPreference -PUAProtection 1
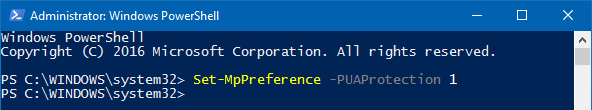
This PowerShell command adds a registry value to the following key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender
- Value: PUAProtection
- Data: 1 – enables PUA protection | 0 – disables protection
Note that manually setting the registry value would still work. But the above registry path is protected and can’t be edited using the Registry Editor unless you’re editing it as SYSTEM.
Method 2: Enable PUA Protection Manually [Registry Location 2]
This method uses the same registry value but implements it under the Policies registry key.
Start Regedit.exe and go to the following key:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender
Create a DWORD value named PUAProtection
Double-click PUAProtection and set its data to 1.
Method 3: Enable PUA Protection Manually [Registry Location 3]
Start the Registry Editor (regedit.exe) and go to the following key:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender
Create a subkey named “MpEngine”
Under MpEngine, create a DWORD value named MpEnablePus
Double-click MpEnablePus and set its value data to 1
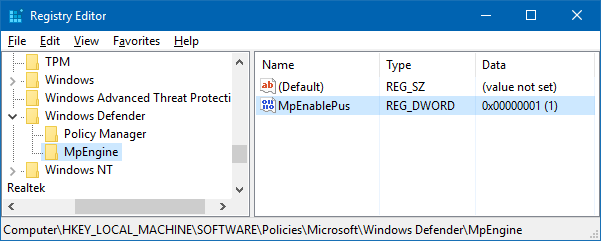
This configures Windows Defender to enable real-time scanning and removal of “Potentially Unwanted” stuff.
Exit the Registry Editor.
Of those three methods, 1 & 2 are not yet documented by Microsoft — but I managed to find them out when playing with PowerShell. Methods 1 & 2 were tested in a system running Windows 10. Method 3 was initially published by the MMPC blog.
Apply the changes
Do one of these things to apply the changes:
- Turn off real-time protection, and turn it back on.
- Update Windows Defender definitions
- Restart Windows
PUA will be blocked only at download or install time. A file will be included for blocking if it meets one of the following conditions:
- The file is being scanned from the browser
- The file has Mark of the Web (Zone ID) set
- The file is in the Downloads folder
- The file in the %temp% folder
Does Windows Defender PUA Protection work on systems not part of an enterprise network?
The Microsoft Malware Protection Center (MMPC) blog announced this opt-in Windows Defender feature last year. But, as the MMPC blog post references only “enterprise” systems, some home users may be wondering whether or not the PUA detection feature works on standalone computers.
Yes. Windows Defender PUA scanning works in standalone systems, as well.
The following test shows that Windows Defender PUA detection certainly works in systems not part of a domain network.
MMPC Security Portal has the complete list of “Potentially Unwanted Programs” or “Potentially Unwanted Applications,” each threat name is prefixed with “PUA:”.
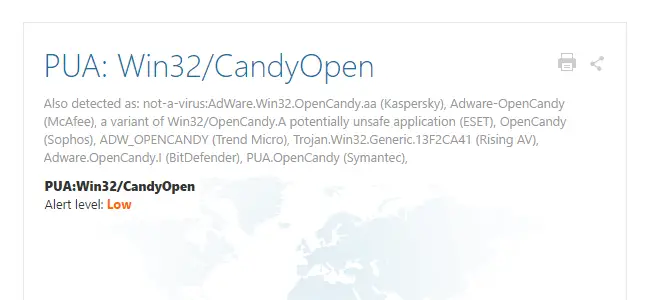
For example, PUA: Win32/CandyOpen is a PUP/PUA bundled with Magical jelly bean Keyfinder and other programs.
(Magical Jelly Bean Keyfinder, otherwise, is a useful piece of software.)
Before activating Windows Defender PUA protection, I downloaded Magicaljellybean’s Keyfinder and tried to run it on a Windows 10 v1607 standalone computer. Windows Defender allowed me to download the installer and run it.
After setting the “MpEnablePus” value data to 1 using the Registry Editor and updating the definitions, Windows Defender blocked the setup program from running.
Also, when I tried to download a new copy of the Keyfinder installer, the file was blocked as it landed up in the Downloads or %temp% folder. The result was the same when I chose a folder other than “Downloads”.
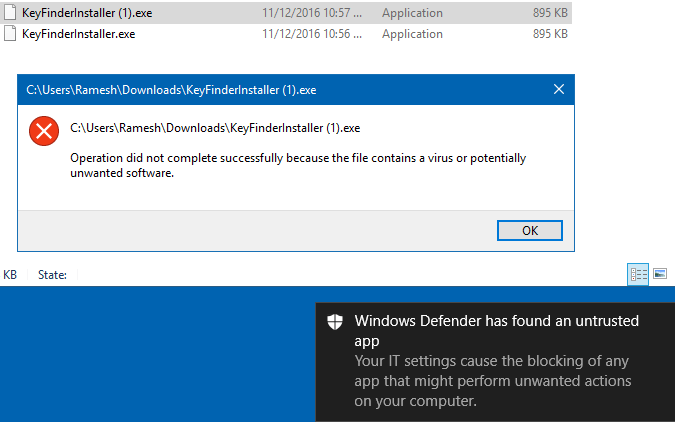
And the Windows Defender notification message was shown.
Windows Defender has found an untrusted app
Your IT settings cause the blocking of any app that might perform unwanted actions on your computer
Whereas, the notification message verbatim is different for “malware” detections, in which case it would say “Found some malware.”

And the PUA was quarantined, as shown in the Windows Defender scan history.
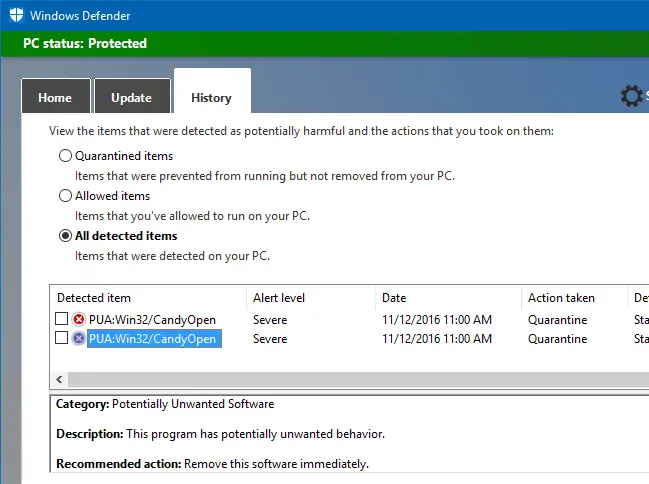
Magical Jelly Bean Keyfinder seems to bundle different PUAs in its installer from time to time. For example, when tested in May 2019, the installer contained another PUA (named PUA:Win32/Vigua.A) with threat level “Severe.”
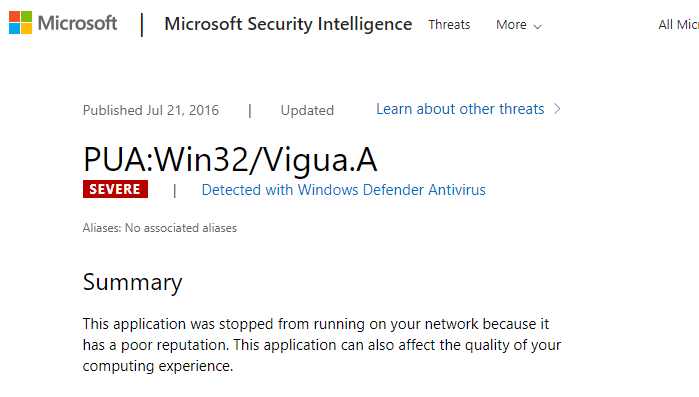
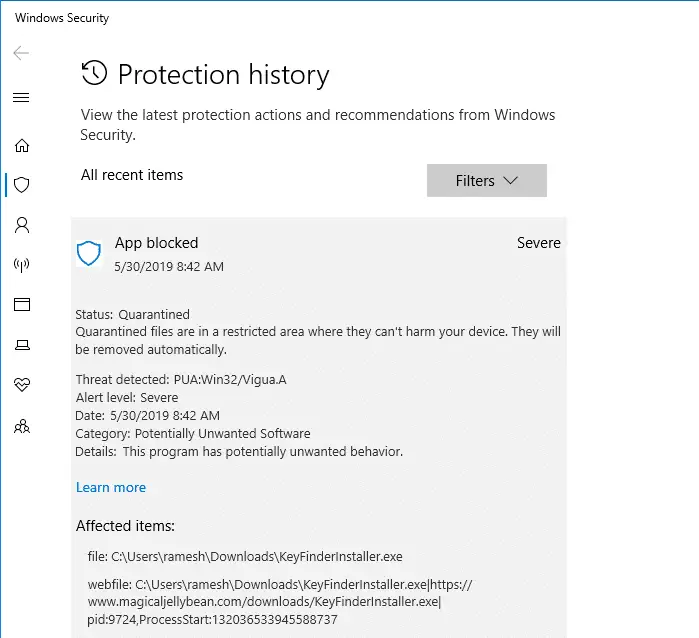
The notification message is different this time. It said, “Windows Defender Antivirus blocked an app that might perform unwanted actions on your device.”
Conclusion: The Windows Defender PUA detection feature can be handy for systems that don’t already leverage a third-party premium anti-malware solution (e.g., Malwarebytes Antimalware Premium) with real-time monitoring. I Hope Microsoft adds a GUI option to enable the PUA scanning feature in Windows Defender, like the Limited Periodic Scanning opt-in feature (and the GUI option) in Windows 10.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!
How can we enable Windows Defender in 1511 so that it runs periodically alongside of another AV program? Otherwise this fix would never run.
@Ted: Limited Periodic Scanning can’t be enabled in v1511. You may scan with WDO instead, using PowerShell.
Hi. I just wanted to know if the PUAProtection DWORD value and the MpEngine key will clash if I were to do both.
If “PUAProtection” and “MpEnablePus” – both are set to 1 then there won’t be any problems.