Many Windows system files, registry keys, and services are owned by the SYSTEM (a.k.a LocalSystem) account, which has a high privilege level. If you need to modify a registry key owned by the SYSTEM account, there are at least two options.
The first option that comes to your mind is to take ownership of the corresponding registry key, assign yourself Full Control permissions. Once the registry key or the values are updated, revert the permissions and ownership to SYSTEM.
There is, however, an easier option. You can run the program — e.g., the Command Prompt or the Registry Editor under the SYSTEM account directly and update the registry values.
This article lists 7 different methods using which you can run programs under the SYSTEM or LocalSystem account in any version of Windows, including Windows 10. You can also add a Run as SYSTEM right-click menu option for .exe files.
Method to run a program under the SYSTEM account:
Before proceeding, understand that the terms SYSTEM, LocalSystem, and NT AUTHORITY\SYSTEM are one and the same.
How to Run Programs as SYSTEM (LocalSystem account)
To run a program under the SYSTEM account, use one of the following tools:
Using PsExec.exe from Windows Sysinternals
Use PsExec.exe console tool from Microsoft’s Windows Sysinternals to run a program under the SYSTEM context. Follow these instructions:
- Download PsExec from Microsoft Sysinternals.
- Unzip and extract the tool to a permanent folder — e.g.,
d:\tools - Open an elevated or admin Command Prompt window.
- To start the Registry Editor under the SYSTEM account, type the following command, and press ENTER:
d:\tools\psexec.exe -sid c:\windows\regedit.exe
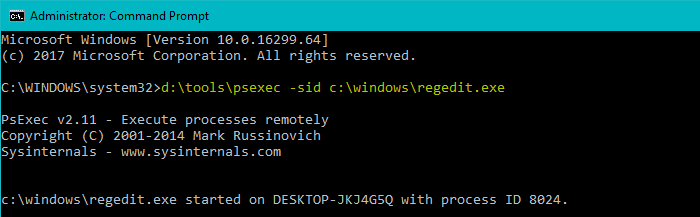
The above
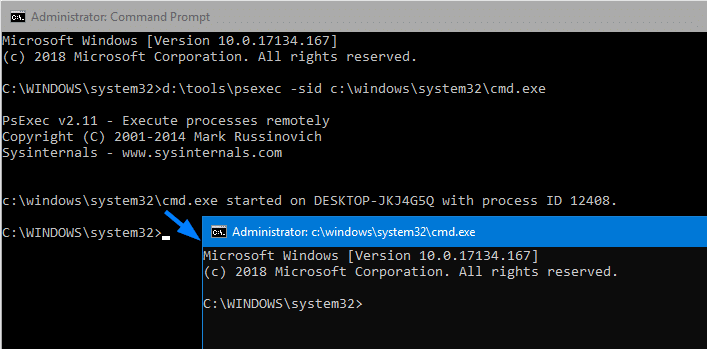
PsExeccommand-line starts the Registry Editor underLOCALSYSTEMaccount so that you can modify protected areas in the registry.Note: If you launch Command Prompt (
cmd.exe) using PsExec.exe under theSYSTEMaccount, it spawns a new Command Prompt window. And, any program you launch from that Command Prompt window would run under theSYSTEM(LocalSystem) account, which is a high privileged account. You must be cautious when running programs under the SYSTEM account so that you don’t accidentally run an undesired program asSYSTEM.
- In the Registry Editor window, go to the desired registry key and modify the values you want.
(For instance, you may want to fix the “Startup type” of Task Scheduler service or the Windows Update service in the registry.) - Exit the Registry Editor.
Using Advanced Run from Nirsoft
AdvancedRun is a simple tool for Windows that allows you to run a program with different settings that you choose, including – low or high priority, start directory, main window state (Minimized/Maximized), run the program with different user or permissions, Operating system compatibility settings, and environment variables. You can also save the desired settings into a configuration file and then run the program automatically from the command-line with the desired settings.
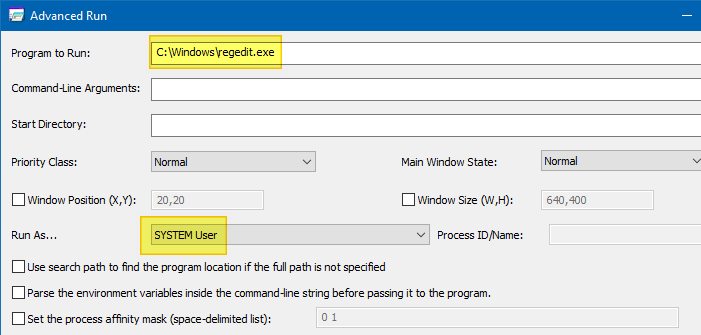
Using Advanced Run, you also launch a program under SYSTEM or a different user context.
Type in the program name to run and choose SYSTEM user in the Run As dropdown box, and click Run.
You can also create a desktop shortcut to run a program as SYSTEM. Here is the command-line syntax you use:
AdvancedRun.exe /EXEFilename "C:\Windows\regedit.exe" /RunAs 4 /Run
/RunAs 4 instructs to start the program under the LocalSystem account. The possible value data for the /RunAs switch are below:
1– Run as current user (elevate)2– Run as current user (no elevation)3– Run as Administrator (force elevation)4– Run as SYSTEM8– Run as TrustedInstaller
This starts the program under the LocalSystem account, which you can verify in the Task Manager Details tab.
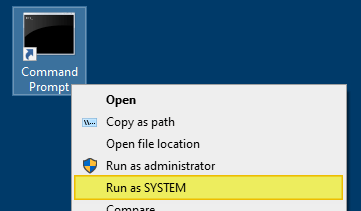
Run as SYSTEM via the right-click menu
To launch a program under the SYSTEM account (with Advanced Run) from the right-click context menu, make a .reg file from the following contents and run the file.
Windows Registry Editor Version 5.00 [HKEY_CLASSES_ROOT\exefile\shell\runassystem] @="Run as SYSTEM" [HKEY_CLASSES_ROOT\exefile\shell\runassystem\command] @="d:\\tools\\AdvancedRun.exe /EXEFilename \"%1\" /RunAs 4 /Run"
Change the path to AdvancedRun.exe in the .reg file if necessary.
This adds the Run as SYSTEM command to the right-click menu for .exe files and its shortcuts.
Using Process Hacker
Process Hacker is an excellent process manager that looks similar to Sysinternals Process Explorer. This tool has a unique feature that allows you to launch a program under the same account as a running process or service.
- Run Process Hacker as administrator.
- Locate a program or service which is currently running under
NT AUTHORITY\SYSTEM. - Right-click on the process, click Miscellaneous, and click Run as this user…
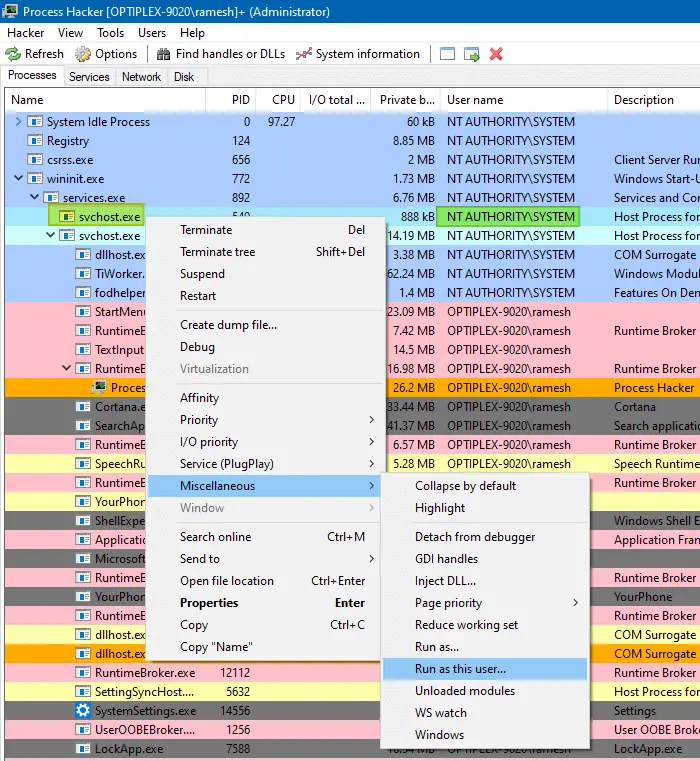
- Select the program (e.g., regedit.exe, or cmd.exe) you want to launch as that user.
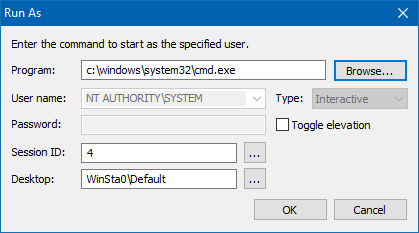
- Click OK.
Now the program (e.g., cmd.exe) would run as SYSTEM (NT AUTHORITY\SYSTEM)
The above method can also be used to launch any program under TrustedInstaller.
Using NirCmd.exe from NirSoft
NirCmd is a multipurpose command-line tool which we’ve covered in this site before.
NirCmd can start a program elevated as well as launch it under the SYSTEM account.
Use this command-line to start the Registry Editor elevated and under the SYSTEM account:
nircmd.exe elevatecmd runassystem c:\windows\regedit.exe
Context menu implementation
Make a .reg file from the following contents and run the file.
Windows Registry Editor Version 5.00 [HKEY_CLASSES_ROOT\exefile\shell\runassystem] @="Run as SYSTEM" [HKEY_CLASSES_ROOT\exefile\shell\runassystem\command] @="d:\\tools\\nircmd.exe elevatecmd runassystem \"%1\""

Using RunAsSystem from Uwe Sieber
RunAsSystem (from Uwe Sieber) is a console tool that launches a program under the SYSTEM account or context. It also passes the window style and its process priority to the executed process by default. You can override the window size as well as the child process priority using command-line arguments. Uwe Sieber is the one who developed the famous USB Drive Letter Manager program.
It waits for the started process to end and then passes back its return code (aka errorlevel). However, in a batch file, you have to add start /wait.
Usage:
RunAsSystem [-min|-max|-normal|-noact|-hid] [-low|-below|-normal|-above|-high] "executable" [params for executable]
Examples:
RunAsSystem "C:\Windows\notepad.exe" RunAsSystem "%windir%\regedit.exe" RunAsSystem "%windir%\System32\cmd.exe" /k dir /s "C:\System Volume Information"
Context menu implementation
Make a .reg file from the following contents and run the file.
Windows Registry Editor Version 5.00 [HKEY_CLASSES_ROOT\exefile\shell\runassystem] @="Run as SYSTEM" [HKEY_CLASSES_ROOT\exefile\shell\runassystem\command] @="d:\\tools\\RunAsSystem.exe \"%1\""
The above .reg file adds a Run as SYSTEM command in the right-click menu for .exe files. The .reg file assumes that the file RunAsSystem.exe is placed under the d:\tools folder. If not, alter the path accordingly in the .reg file.
Using “NSudo” from M2Team
NSudo (GitHub) is a similar portable utility like Advanced Run, except that it is not digitally signed. It can launch programs under SYSTEM, Current User, Current Process, or the TrustedInstaller account. We’ve earlier seen how to use NSudo to launch programs as TrustedInstaller.
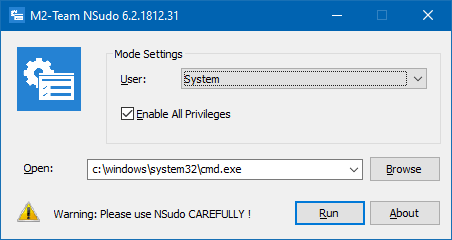
Select the mode (System) from the dropdown, type in the executable path, and click Run.
Optionally, you can also add a predefined set of programs or commands in the Open: drop-down list box by editing the file named NSudo.json located in the same folder as the executable.
To run a program under the SYSTEM context using NSudo command-line, use this syntax:
NSudo -U:S c:\windows\system32\cmd.exe
See below for the full list of command-line arguments supported by this utility.
NSudo: Command-line support
NSudo version 6.2.1812.31 -U:[ Option ] Create a process with specified user option. Available options: T TrustedInstaller S System C Current User P Current Process D Current Process (Drop right) PS: This is a mandatory parameter. -P:[ Option ] Create a process with specified privilege option. Available options: E Enable All Privileges D Disable All Privileges PS: If you want to use the default privileges to create a process, please do not include the "-P" parameter. -M:[ Option ] Create a process with specified Integrity Level option. Available options: S System H High M Medium L Low PS: If you want to use the default Integrity Level to create a process, please do not include the "-M" parameter. -Priority:[ Option ] Create a process with specified [rocess priority option. Available options: Idle BelowNormal Normal AboveNormal High RealTime PS: If you want to use the default Process Priority to create a process, please do not include the "-Priority" parameter. -ShowWindowMode:[ Option ] Create a process with a specified window mode option. Available options: Show Hide Maximize Minimize PS: If you want to use the default window mode to create a process, please do not include the "-ShowWindowMode" parameter. -Wait Make NSudo wait for the created process to end before exiting. PS: If you don't want to wait, please do not include the "-Wait" parameter. -CurrentDirectory:[ DirectoryPath ] Set the current directory for the process. PS: If you want to use the NSudo's current directory, please do not include the "-CurrentDirectory" parameter. -UseCurrentConsole Create a process with the current console window. PS: If you want to create a process with the new console window, please do not include the "-UseCurrentConsole" parameter. -Version Show version information of NSudo. -? Show this content. -H Show this content. -Help Show this content. Context Menu: -Install : Copy NSudo to the Windows directory and add the context menu. -Uninstall : Remove NSudo in the Windows directory and the context menu. PS: 1. All NSudo command arguments is case-insensitive. 2. You can use the "/" or "--" override "-" and use the "=" override ":" in the command line parameters. For example, "/U:T" and "-U=T" are equivalent. 3. To ensure the best experience, NSudoC does not support context menu. Example: If you want to run Command Prompt with TrustedInstaller, enable all privileges and the default Integrity Level. NSudo -U:T -P:E cmd
Context menu addition
- Run NSudo with
-Installparameter. It copies NSudo to the Windows directory and adds the context menu. - To remove the context menu, run NSudo with the
-Uninstallparameter. It removes NSudo from the Windows directory and the context menu.
RunX from d7xTech
RunX is a digitally signed executable that can launch any process with a Local System account or TrustedInstaller account privileges. It is also designed to optionally pass command line arguments to that app without having to open an admin Command Prompt window and navigate to the appropriate path first. It can also capture and display the program’s exit code.
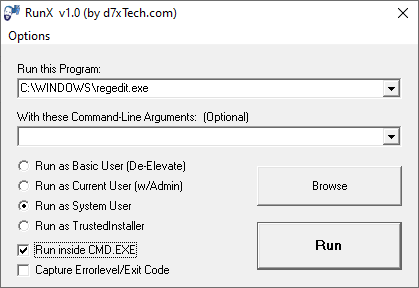
The “Run inside CMD.EXE” option will launch Command Prompt window first and launch the target program from there. That way you can see the exit code in the Command Prompt window or run subsequent commands under System privileges.
Download RunX and RunXcmd from:
New App: RunX and RunXcmd – d7xTech.com (formerly Foolish IT): https://www.d7xtech.com/new-app-runx-and-runxcmd/
The package also includes a console version of the tool named RunXcmd. It’s designed to do the above but for scripting purposes, when you need your script to wait on the process you are running to terminate, and/or when you or your script needs to know the process exit code via %errorlevel% output.
Here’s the list of command-line switches it supports:
Usage: RunXcmd.exe /exec="[path\file.exe]" /wait /account=[user|system|ti] /args=[] Arguments: /exec="[path\file.exe]" (Required; must be wrapped in quotes.) /wait (Optional, Wait for the app to finish; useful in scripting. RunX also returns the /exec file's exit code as it's own.) /account=[user|system|ti] (Optional, Run as User(Non-Admin), System, or TrustedInstaller. If this switch is not specified, TrustedInstaller is assumed.) /args= (Optional, must be the LAST switch, everything after this is passed to the /exec file. Do NOT wrap args in quotes, unless you intend for the quotes to be passed to the /exec file.) Example: (Run as Standard User with Arguments) RunXcmd.exe /exec="c:\path\file.exe" /account=user /args=/Arg1 /Arg2 /Etc. Example: (Run as Trusted Installer and Wait/Return Exit Code) RunXcmd.exe /exec="c:\path\file.exe" /wait
Editor’s Pick: Advanced Run for GUI (and CLI), and PsExec for CLI.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!
This is a really useful article and information. Thank you for that!
I use this feature at the login screen by renaming a few files while Windows is offline. While this is a handy feature for technicians like myself, shouldn’t this be a security issue that Microsoft addresses?
We use psexec to connect to remote Windows machines and sometimes need to be System.
Thank you!