Sometimes, you may need to edit the Windows registry offline to rectify a situation where Windows doesn’t boot after modifying some settings recently. Windows Recovery Environment (WinRE) is a handy platform that provides various system recovery options to diagnose and repair an unbootable Windows installation.
This post explains how to edit the Windows registry offline via Recovery Environment. The screenshots are from a Windows 10 computer. The instructions apply to Windows 11 as well.
How to Edit Windows Registry Offline
Step 1: Accessing the Recovery Environment
Press WinKey+X. Click Shut down or sign out, press and hold the SHIFT key and click Restart. In Windows 10, you can also open Settings (WinKey + i), click Update and Security, click Recovery, and click the Restart Now button under Advanced Startup.
To access Windows RE on an unbootable computer, boot the system using your Windows setup USB disk and access the Recovery Options. Or you may use the Recovery drive if you’ve created one already.
See also: How to access Windows Recovery Environment (WinRE)
Have the BitLocker key ready if you’ve enabled BitLocker drive encryption on the OS drive.
In the Recovery Options, click Troubleshoot.
.png)
Click Advanced options
.png)
At this point, you’ll be offered various recovery options, such as:
- System Restore
- System Image Recovery
- Startup Repair
- Command Prompt
- Startup Settings
- Go back to the previous build
.png)
If a recent software installation or Malware attack has caused your system unbootable, a System Restore rollback would be ideal. On the other hand, if you want to fix a specific registry setting, or to delete a locked-down file or registry key that you can’t otherwise modify when Windows is running, click Command Prompt.
BitLocker-encrypted drive?
Note: If Windows RE is manually started from a repair disk, then the BitLocker recovery key must be provided to unlock the BitLocker–protected drives.
If your drive has been encrypted using BitLocker Drive Encryption, you’ll now see the recovery key prompt such as the one below:
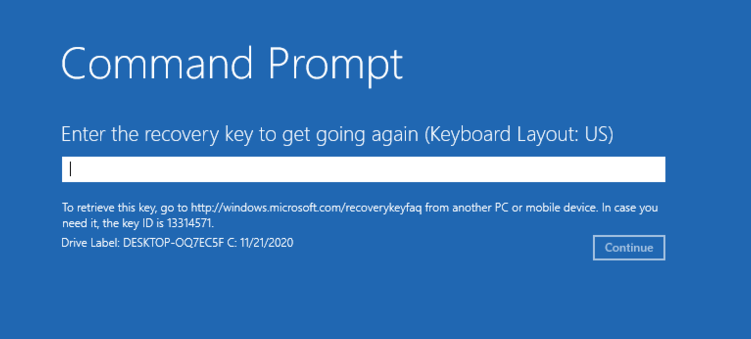
If you’ve forgotten the BitLocker recovery key or lost the printout, you can view the key by signing into your Microsoft account (that’s not the only way, though) and going to this URL:
Microsoft account | BitLocker recovery keys: https://account.microsoft.com/devices/recoverykey Find my BitLocker recovery key: https://support.microsoft.com/en-us/windows/find-my-bitlocker-recovery-key-fd2b3501-a4b9-61e9-f5e6-2a545ad77b3e
Even if you launch Command Prompt using the Shift + F10 key combination (bypassing the BitLocker recovery screen) or clicking the “Skip this drive” option, you won’t be able to access the encrypted drive. You’ll be asked to unlock the drive via Control Panel.
In my case, I haven’t enabled BitLocker Drive Encryption. So, no BitLocker prompt appeared.
.png)
Select your Windows user account, type the password on the next screen, and click Continue.
(If you’ve booted into Windows RE using the Windows installation or repair disk, you wouldn’t see the password prompt below.)
.png)
.png)
Command Prompt window would now show up.
Step 2: Find your Windows drive letter (in Windows RE)
The next job is to find the drive letter of your Windows installation, as seen from Windows RE. This can be done by running the bcdedit /enum osloader command.
Important: If you’re accessing Windows RE using a bootable setup or recovery disk, run “bcdedit /enum osloader“. Else, running “bcdedit” should be sufficient.
.png)
In the BCDEDIT command output, look for the boot loader entries containing the fields, namely, path (mentioning winload.exe or winload.efi) or osdevice or systemroot, and make a note of the drive-letter, which in this case, is D:\
It doesn’t have to be D:\ in every case; Depending upon the computer, the Windows drive letter (as seen from Windows RE) may be C:\ itself. It’s advisable to run bcdedit /enum osloader anyway.
Step 3: Edit the Windows Registry Offline via WinRE
(As per the output in Step 2 above, your Windows installation is in D: drive in this example.)
In the Command Prompt window, type REGEDIT and press Enter to launch the Registry Editor.
In the Registry Editor, select the HKEY_USERS hive.
Click the File menu, and click Load Hive…
.png)
The Load Hive… option would be available if you’re currently in HKEY_USERS or HKEY_LOCAL_MACHINE. In this case, we select HKEY_USERS and click the Load Hive.. option.
INFO: Registry hives list
Registry hives are database files that store data. Here is the list of common registry hives and their description.
| Registry Hive Filename | Registry Key Location (in your Windows installation) | Description |
| %windir%\system32\config\SAM | HKEY_LOCAL_MACHINE\SAM | Stores the local user account info and passwords. |
| %windir%\system32\config\SYSTEM | HKEY_LOCAL_MACHINE\SYSTEM | Contains services/devices/LKG configuration, etc. |
| %windir%\system32\config\SOFTWARE | HKEY_LOCAL_MACHINE\SOFTWARE | Contains entries added by programs, Product keys. |
| %windir%\system32\config\DEFAULT | HKEY_USERS \.Default | Profile used by the Local System account |
| %userprofile%\ntuser.dat | HKEY_CURRENT_USER | User registry hive. Stores per-user settings. |
| %localappdata%\Microsoft\Windows\usrClass.dat | HKEY_CURRENT_USER\Software\Classes | User registry hive. Stores per-user file association settings. |
(In our case, we need to load the SOFTWARE registry hive and edit the Winlogon → UserInit registry value. However, if you need to modify the services configuration or startup type, you need to load the SYSTEM registry hive instead of SOFTWARE.)
Browse or type the path to the SOFTWARE registry hive of your Windows installation, which is in D:\ drive in this example, as per the output in “Step 2“.
The path to the SOFTWARE registry hive of your Windows installation (when seen from Windows RE) would be “d:\windows\system32\config\software“. Type the path and click Open.
.png)
Mention a name for the loaded hive.. it can be anything.
.png)
The SOFTWARE registry key is now mounted to a branch named MyKey.
.png)
The loaded SOFTWARE hive (MyKey) is nothing but the following registry path of your Windows installation:
HKEY_LOCAL_MACHINE\Software
Fixing a Registry Key/Value
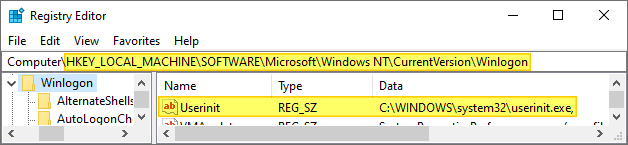
Let’s assume you want to fix the Userinit registry value, which was modified by malware, and you cannot log on to your profile. To fix the Userinit value, go to the following branch:
HKEY_USERS\MyKey\Microsoft\Windows NT\CurrentVersion\Winlogon
Double-click the Userinit value, and fix the path accordingly.
.png)
Note: You’ll need to use the actual path to your Windows installation (NOT the Win RE assigned drive letter D:). If Windows is installed in C:\, then the Userinit registry value data should be:
C:\Windows\System32\Userinit.exe,
(You must include the trailing comma as well)
Related post: Here is a case where malware had modified the Userinit value (and locked down the Task Manager in some systems), thus blocking the user from logging on to their user account. Check out the article Fix “Can not find script file C:\WINDOWS\run.vbs” for more information.
Once the changes are made, it’s time to Unload the hive. To do so, go back to the “MyKey” branch, click the File menu, and choose Unload Hive…
.png)
That’s it! Type EXIT in the Command Prompt window. Continue to Windows.
Optionally, once you’re successfully logged on to your user account, load the Registry Editor, and you’ll see that the value you modified offline is reflected there.
The above step is not needed anyway. It’s just in case you’re curious if the offline registry editing has worked.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!
It worked .. wow, your amazing and I love you hahha
Seriously thank you ??
You’re very welcome Novs.
You sir, have saved my PC. Thanks for the knowledge. I’m now trying to get AVG to remove the malware permanently and uninstalling all the malware affiliated software. Thank you sooo much
@Kson. Glad this guide helped. Thanks for the feedback.
Thanks you a lot, you saved my pc.
You’re the best 😉
@Chris: You’re very welcome!
Thank you from Barcelona (Catalunya), you save my work.
@Jordi: You’re welcome!
Hi Ramesh. This is a fantastic tutorial, as are all your blog entries. When I was working this example, I performed “load hive” on the HKEY_LOCAL_MACHINE branch because I wanted to check out whether the CurrentControlSet subkey exists offline. As I suspected, it does not. Went I went to perform “unload hive” on the HKEY_LOCAL_MACHINE branch, that option was not available. However, it was available on “MyKey” so I unloaded that temp hive. I then performed the load hive on the HKEY_USERS branch and the same thing happened (unload hive option was only available on “MyKey”). Does this sound right?
Nancy: You’re correct. Unload hive appears only when the loaded hive is selected. I’ll update the post. Thanks.
Load Hive…
Unload Hive…
Are all Gray – any idea why?
Which root key you’re in?
Great tutorial, thanks
You saved my ars, and my gaming rig!!!
For Info:
Updated Win 10 to 19xx
Steam does not start correct, always at 3 time!
Disabled ram compression all ok
regedit services ipxx and RT values to start 1 (instead of 2)
Reboot loop
Got ashen!
started NB – searched google for “window 10 edit registry in restore mode
clicked all the entries, till found your in place 5 (after all usless infos and ads)
got ashen again at the point “load hive” is grayed! Paniced!
googled again – found entry in superuser
back to ur site, reread the part, face palm ! you had wrote it …
loaded hive, reseted all the service remembered to start 2 or 3.
Unloaded, restarted, took 10 seconds longer, ashed again at the blank screen!
BAM login was there !
Thank you, you made the job MS disabled:
Registry auto backup and load last state!
I did what you said, but nothing changed. I went back to the registry editor and none of my changes were saved.
Never mind, I solved my own problem.
Thank you so much for your tutorial!
While loading hive, I am getting below error:
Cannot Load X:\Windows\System32\config\SOFTWARE: The process cannot access the file because it is being used by another process.
@Nitin: Use the correct drive-letter. When you’re in WinRE X:\ will be drive-letter for WinRE environment, and not the drive-letter of your Windows installation. Use Bcdedit as mentioned in the article to find out the right drive-letter.
You are my hero, thankyou now i can log in to windows, because i accidentally running chkdsk and somehow stuck at 10% and i followed loading hive as your instructions but in “system” hive and edit bootexecute for autochk as default and poof work as magic after hours
THank you this help me get out of a huge mess. 🙂
Let’s say you exported the registry to a file when the system was in an OK state. How would you restore this backup from the WinRE?
For…abstract reasons, my installation now freezes some random (but relatively short — i.e. short enough that I’m afraid of even running an upgrade install at this point) time following each reboot. At first I thought it was the GPU driver…but the more I tried to fix it, the more heinous the problem seemed to be getting.
So anyway, I created an export of the registry (using RegEdit -> Right click Computer & Export) a few weeks ago, which I’m now thinking of restoring. But when I try to restore the .reg file, it ends up with an error (same when I try reg.exe import exportfile.reg — in both cases, after minutes, it says error accessing the registry).
I assume this is because the registry is in use on a running system, so perhaps I might have more luck from WinRE…anyway, any ideas?
P.S. I tried to submit this just now and it was blocked, supposedly due to presence of HTML code. If you are seeing this, it means I changed “less than” exportfile “greater than” .reg to exportfile.reg (two paragraphs up). IOW, the blocking mechanism detected a false positive.
I just wanted to say thank you soo much for this tutorial. I literally searched the internet for 4 hrs straight before stumbling on your post. Honestly I don’t know how to thank you. Thank you, thank you, thank you. Thank you again. God bless.
Unbelievable! Saved me having to do a full reinstall. You’re a hero. I’m sure this will prove useful to me again and again.
Hi Ramesh – hoping you can help me. I have 2 profiles on my computer (myself and default account). The default account is the administrator. I don’t want the default account to be the administrator; I need to have administrator access. How can I change that? Thank you!
@Mary: You can change the account type via Settings.
Start > Settings > Accounts > Under Family & other users. Select the account owner name (you should see “Local Account” below the name), then select Change account type.
Thank you for this blog entry. It was very helpful!
@Ramesh,
I am viewing your post due to having the sihost.exe Unknown Hard error issue.
I edited the registry to disable some services, and now the disabled services make this error.
How to fix? I had a registry backup, but it appears the filesize is less than other saves–and so I maybe able to restore the OS.
What software can edit the registry offline? Related, is there a generic Win 10 Registry I can restore?
Not only it worked but it solved an issue I had with the trackpad driver not working not updating (Code 10) for 3 month. I was about to cry with so many BSOD. I just removed the line that I added previously while try to fix the trackpad and which caused the BSOD and voilà it booted AND my trackpad is working now. (TT) (Tears of joy)
This does not seem to work anymore. I am attempting right now to restore backed up registry hives on Win11 Pro 22H2, and it seems Microsoft removed the ability to login mentioned on your article. You can run regedit, but have no permissions to load the hives. Which upsets me. My System Restore never works, it always fails to load files.
It seems changes were made in Win11. You can no longer log in with command prompt in Win11 Pro 22H2 so I don’t have permissions to modify registry hives. This is very unfortunate.
I successfully got through all steps of this guide until I get up to “unload hive”
When I click this an error message pops up saying “Cannot unload MyKey: Access is denied”
Any suggestions about where I’ve gone wrong or how to fix this?
Thanks,
Phil
@Phil: Close Regedit.exe and reopen it. Try to unload the hive now.