A new malware emerged in the 1st week of August 2023 that has infected many computers already. The origin of the malware is yet to be traced, but the malware adds six scheduled tasks, each of which runs rhc.exe, wscript.exe agile2.vbs, ytcheckts.vbs, and php.exe.
Here’s how to remove the infection.
Resolution
Step 1: Run TrendMicro online scanner
First, run TrendMicro Online Scanner, as it seems to be effective for this malware. Please visit the following link to download the scanner.
Free Online Virus Scan | Trend Micro: https://www.trendmicro.com/en_in/forHome/products/housecall.html
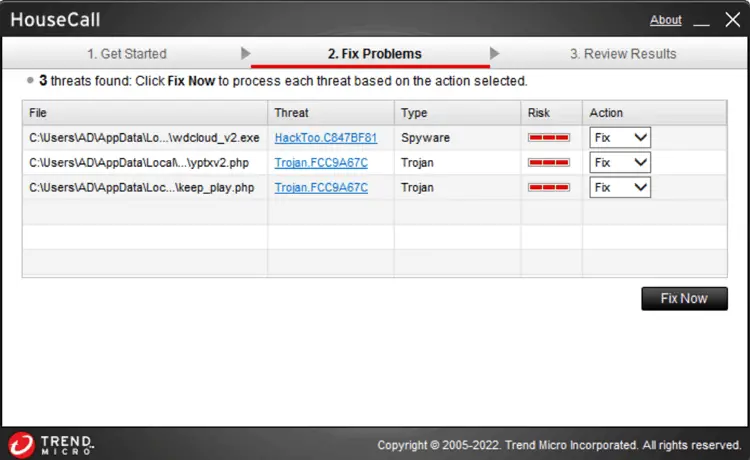
(Img Src: Microsoft Answers)
Step 2: Remove the rogue tasks and folders
Option 1: Run ypsx_remove.bat
- Download ypsx_remove.bat (zipped) and save it to the desktop.
- Unzip the archive and extract the Batch file to the desktop.
- Right-click “ypsx_remove.bat” and choose Run as administrator.
The batch file removes the rogue scheduled tasks and the folders typically added by the malware.
Option 2: Run the commands manually.
Open an admin Command Prompt and run these commands one by one:
schtasks.exe /delete /tn "\WDNA" /f schtasks.exe /delete /tn "\WDNA_LG" /f schtasks.exe /delete /tn "\YTPX Cloud LG" /f schtasks.exe /delete /tn "\YTPXCheck" /f schtasks.exe /delete /tn "\YTPXCheck LG" /f schtasks.exe /delete /tn "\VSPXService" /f schtasks.exe /delete /tn "\VSPXService_LG" /f schtasks.exe /delete /tn "\WNVIDIA_FACTORY_LG" /f schtasks.exe /delete /tn "\wupdatecloud" /f schtasks.exe /delete /tn "\wupdatecloud_LG" /f schtasks.exe /delete /tn "\ServiceGPUTaskUpdate" /f schtasks.exe /delete /tn "\APTXService" /f schtasks.exe /delete /tn "\APTXService_LG" /f schtasks.exe /delete /tn "\Window Update" /f taskkill /f /im php.exe taskkill /f /im rhc.exe rd /s /q "%AppData%\ypsx_cloud_v2" rd /s /q "%AppData%\wupdater_cloud" rd /s /q "%AppData%\ContentCloud" rd /s /q "%LocalAppData%\wupdater_cloud" rd /s /q "%LocalAppData%\ContentCloud" rd /s /q "%LocalAppData%\CDContent" rd /s /q "%LocalAppData%\WDZCloud" rd /s /q "%LocalAppData%\ypsx_cloud_v2" rd /s /q "%LocalAppData%\updates" rd /s /q "%LocalAppData%\HintonJer" rd /s /q "%LocalAppData%\KbLobs" rd /s /q "%LocalAppData%\wtraff_cloud" powershell.exe -command gci $env:Appdata -filter 'rhc.exe' -depth 3 powershell.exe -command gci $env:LocalAppdata -filter 'rhc.exe' -depth 3
The last two commands verify if the unneeded program still exists (perhaps under a different folder name) on the disk. If rhc.exe appears in the directory listing, delete the parent folder manually.
Important
The above Batch file removes the entries typically added by this specific malware. Your computer may be infected by a different version of this malware that uses other folder names. Following up with a manual verification using Autoruns or the Farbar Scanner tool is best.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!