Microsoft Defender Offline is an antimalware scanning tool that lets you boot and run a scan from a trusted environment. It utilizes Windows RE to run the offline scan.
During the Microsoft Defender Offline scan, it may appear to the user that the scan stalled or crashed at 91%, 92%, or 93% on some systems. This article tells you how to check if the last Microsoft Defender Offline scan was completed correctly.
Cause
The “Percent complete” indicator in the Microsoft Defender Offline scan is entirely inaccurate. For example, check these images.
92622 files have been scanned. The percentage is 93.

95417 files have been scanned. The percentage remains at 93.
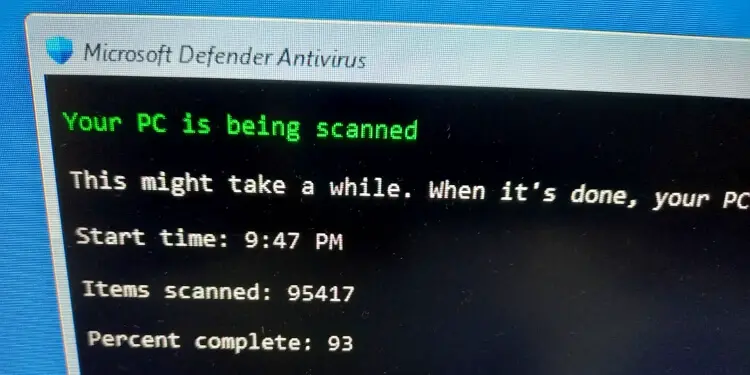
115417 files have been scanned. The percentage remains at 93.
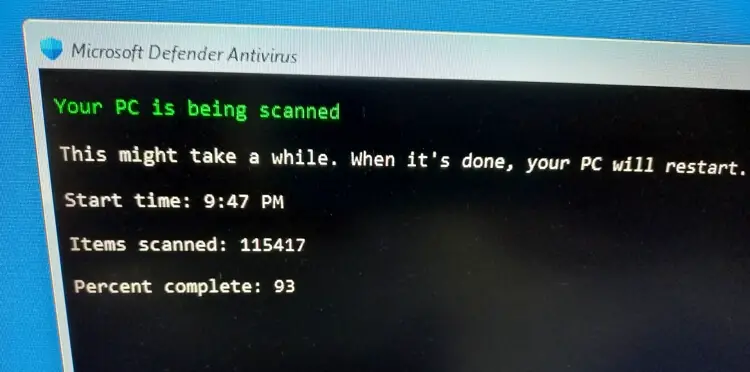
As long as the number in the “Items scanned” increases, it means scanning progresses well.
It’s OK if Microsoft Defender Offline closes and reboots the computer before the progress percentage reaches 100%. Not sure on what basis the “percent complete” value is calculated, but it’s not even approximate. Therefore, the field should be ignored completely.
Check the status of the last Offline Scan
To correctly know the status or the return code of the previous Microsoft Defender Offline scan, inspect the msssWrapper.log file. The log file is located in the following path:
C:\Windows\Microsoft Antimalware\Support\msssWrapper.log
The recent entries are at the bottom of the log. Open the log using Notepad and scroll to the bottom part of the file.
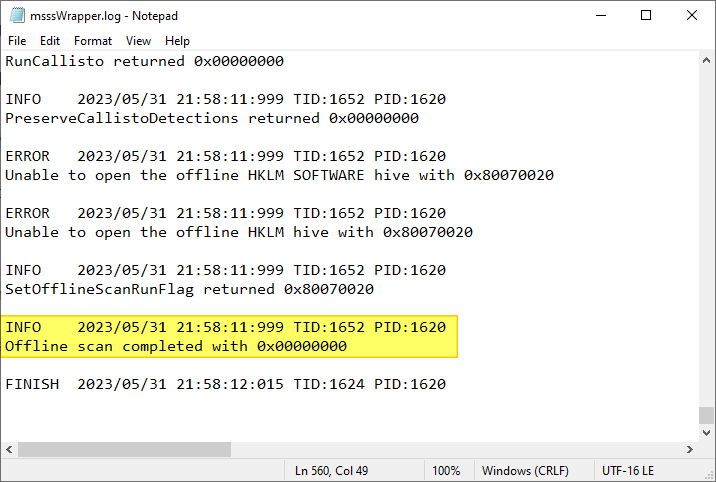
If you see the following line at the end of the log, it means the last scan ran correctly.
Offline scan completed with 0x00000000
(Code 0 or 0x00000000 means SUCCESS.)
The Microsoft article Microsoft Defender Offline in Windows | Microsoft Learn states the following:
Where can I find the scan results?
To see the Microsoft Defender Offline scan results:
- Select Start, then Settings > Update & Security > Windows Security > Virus & threat protection.
- On the Virus & Threat protection screen, under Current threats, select Scan options and Protection history.
Screenshots:
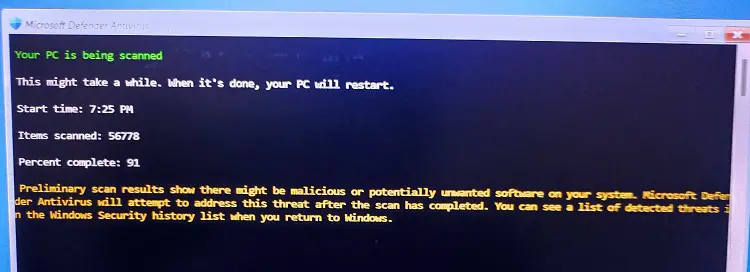
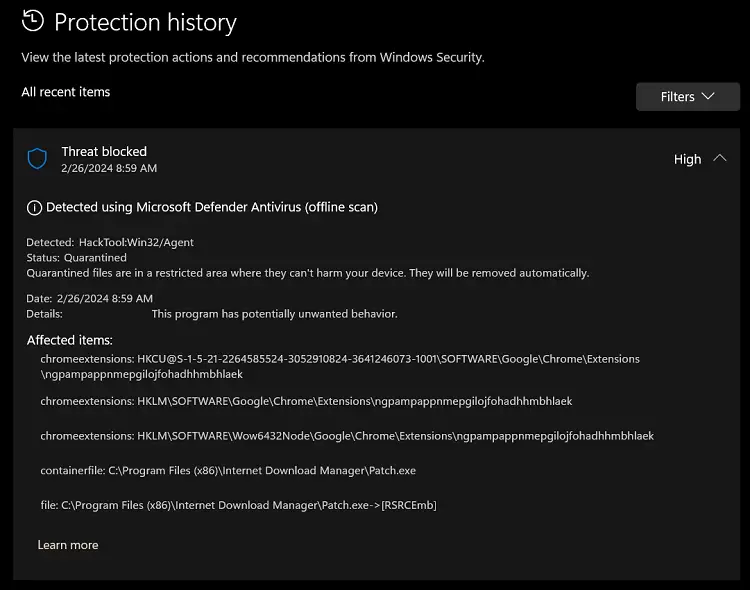
Malware detected using Microsoft Defender (offline scan) – Protection history page
However, the above applies only if the offline scan detected malware. Else, the Protection history page doesn’t show anything about the last offline scan.
INFO: A sample msssWrapper.log file
Here are the contents of a sample msssWrapper.log file.
START 2024/04/28 15:48:41:800 TID:1692 PID:1660
INFO 2024/04/28 15:48:41:800 TID:1692 PID:1660
Loading offline registry library returned 0x00000000
INFO 2024/04/28 15:48:41:800 TID:1692 PID:1660
Binary architecture is amd64
INFO 2024/04/28 15:48:41:831 TID:1692 PID:1660
UtilIsFileExists(E:\WINDOWS\SysWOW64\ntdll.dll) returned 0x00000000
INFO 2024/04/28 15:48:41:831 TID:1692 PID:1660
CheckProcessorArchitecture returned 0x00000000
INFO 2024/04/28 15:48:41:831 TID:1692 PID:1660
Setting target OS key: "E:\WINDOWS"
INFO 2024/04/28 15:48:41:831 TID:1692 PID:1660
SetRecoveryEnvironmentKey returned 0x00000000
INFO 2024/04/28 15:48:41:940 TID:1692 PID:1660
Mapping target OS C drive to WinPE E drive
INFO 2024/04/28 15:48:41:940 TID:1692 PID:1660
Mapping target OS D drive to WinPE C drive
INFO 2024/04/28 15:48:41:940 TID:1692 PID:1660
Mapping target OS E drive to WinPE D drive
INFO 2024/04/28 15:48:41:972 TID:1692 PID:1660
BuildTargetOSDriveMapping returned 0x00000000
INFO 2024/04/28 15:48:41:972 TID:1692 PID:1660
Searching for signatures. Default signature path: ""
INFO 2024/04/28 15:48:41:972 TID:1692 PID:1660
Searching for signatures at root of drives...
WARNING 2024/04/28 15:48:41:972 TID:1692 PID:1660
Missing definitions file in 'C:\mpam-fex64.exe'
WARNING 2024/04/28 15:48:41:972 TID:1692 PID:1660
Missing definitions file in 'D:\mpam-fex64.exe'
WARNING 2024/04/28 15:48:41:972 TID:1692 PID:1660
Missing definitions file in 'E:\mpam-fex64.exe'
WARNING 2024/04/28 15:48:41:972 TID:1692 PID:1660
Missing definitions file in 'F:\mpam-fex64.exe'
WARNING 2024/04/28 15:48:41:972 TID:1692 PID:1660
Missing definitions file in 'X:\mpam-fex64.exe'
INFO 2024/04/28 15:48:41:972 TID:1692 PID:1660
Searching for signatures from installed product on target OS
INFO 2024/04/28 15:48:42:987 TID:1692 PID:1660
Looking for Defender registry key on target OS
INFO 2024/04/28 15:48:42:987 TID:1692 PID:1660
Mapped target os path (C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{F79A0553-A974-4973-A00E-6391E4B00807}) to winpe path (E:\ProgramData\Microsoft\Windows Defender\Definition Updates\{F79A0553-A974-4973-A00E-6391E4B00807})
INFO 2024/04/28 15:48:42:987 TID:1692 PID:1660
Found signatures on the target OS at E:\ProgramData\Microsoft\Windows Defender\Definition Updates\{F79A0553-A974-4973-A00E-6391E4B00807}
INFO 2024/04/28 15:48:43:081 TID:1692 PID:1660
SearchForSignatures returned 0x00000000
INFO 2024/04/28 15:48:44:096 TID:1692 PID:1660
Looking for Defender registry key on target OS
INFO 2024/04/28 15:48:44:096 TID:1692 PID:1660
Mapped target os path (C:\ProgramData\Microsoft\Windows Defender) to winpe path (E:\ProgramData\Microsoft\Windows Defender)
INFO 2024/04/28 15:48:44:205 TID:1692 PID:1660
Initializing offline environment and service...
INFO 2024/04/28 15:48:45:911 TID:1692 PID:1660
XCopySignatures returned hr = 0x0
INFO 2024/04/28 15:48:57:054 TID:1692 PID:1660
GetTempPath2W where sigs would unpack =
INFO 2024/04/28 15:48:57:054 TID:1692 PID:1660
Signatures are already fairly recent. Skipping sig update.
INFO 2024/04/28 15:48:57:054 TID:1692 PID:1660
AS Signature Version: 1.409.569.0
INFO 2024/04/28 15:48:57:054 TID:1692 PID:1660
Engine Version: 1.1.24030.4
INFO 2024/04/28 15:48:57:054 TID:1692 PID:1660
Launching user interface...
INFO 2024/04/28 15:48:57:054 TID:1692 PID:1660
Auto-scan mode selected...
INFO 2024/04/28 15:48:57:069 TID:1692 PID:1660
Registered for notifications
INFO 2024/04/28 15:48:57:069 TID:1692 PID:1660
Automatic scan started
INFO 2024/04/28 15:48:57:069 TID:1692 PID:1660
Launched Console UI, waiting...
INFO 2024/04/28 15:56:19:770 TID:1704 PID:1660
CALLBACK: Scan complete. hResult=0x0, threat count=1
INFO 2024/04/28 15:56:19:770 TID:1692 PID:1660
Wait finished (Scan signaled)
INFO 2024/04/28 15:56:19:770 TID:1692 PID:1660
Getting results from scan...
INFO 2024/04/28 15:56:19:770 TID:1692 PID:1660
Scan completed successfully, attempting to clean any active malware. Number of threats from scan: 1
INFO 2024/04/28 15:56:19:770 TID:1692 PID:1660
STARTING LIST OF DETECTED THREATS:
INFO 2024/04/28 15:56:19:770 TID:1692 PID:1660
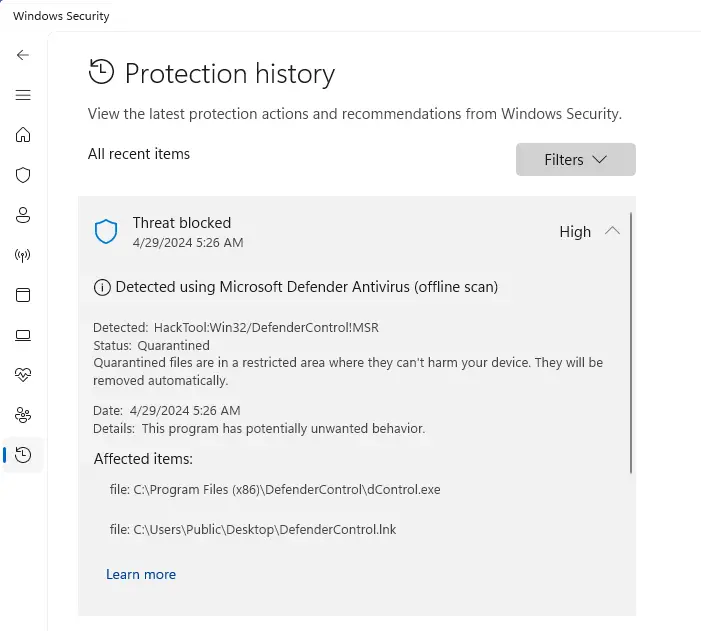
1: Found HackTool:Win32/DefenderControl!MSR (0x80042394).
INFO 2024/04/28 15:56:19:770 TID:1692 PID:1660
Resource 1: Main OS based Path = C:\Program Files (x86)\DefenderControl\dControl.exe WinRE based Path = E:\Program Files (x86)\DefenderControl\dControl.exe.
INFO 2024/04/28 15:56:19:770 TID:1692 PID:1660
Resource 2: Main OS based Path = C:\Users\Public\Desktop\DefenderControl.lnk WinRE based Path = E:\Users\Public\Desktop\DefenderControl.lnk.
INFO 2024/04/28 15:56:19:770 TID:1692 PID:1660
LIST OF DETECTED THREATS COMPLETE. Found 0 threats requiring user-defined action.
INFO 2024/04/28 15:56:19:770 TID:1692 PID:1660
STARTING CLEANING (using default action on all detected threats):
INFO 2024/04/28 15:56:25:051 TID:1692 PID:1660
CALLBACK: Scan complete. hResult=0x0, threat count=1
INFO 2024/04/28 15:56:25:472 TID:1692 PID:1660
Remediation: Successfully completed action Quarantine on threat 0x80042394.
INFO 2024/04/28 15:56:25:472 TID:1692 PID:1660
CLEANING COMPLETE.
INFO 2024/04/28 15:56:25:488 TID:1692 PID:1660
RunCallisto returned 0x00000000
INFO 2024/04/28 15:56:25:535 TID:1692 PID:1660
PreserveCallistoDetections returned 0x00000000
ERROR 2024/04/28 15:56:25:535 TID:1692 PID:1660
Unable to open the offline HKLM SOFTWARE hive with 0x80070020
ERROR 2024/04/28 15:56:25:535 TID:1692 PID:1660
Unable to open the offline HKLM hive with 0x80070020
INFO 2024/04/28 15:56:25:535 TID:1692 PID:1660
SetOfflineScanRunFlag returned 0x80070020
INFO 2024/04/28 15:56:25:535 TID:1692 PID:1660
Offline scan completed with 0x00000000
FINISH 2024/04/28 15:56:25:535 TID:1664 PID:1660
The above log shows that a threat was found and remediated. It’s also shown in the Protection history page.
Editor’s note: In addition to msssWrapper.log, you may find the following logs helpful.
C:\Windows\Microsoft Antimalware\Support\MPDetection-[date]-[time].log C:\Windows\Microsoft Antimalware\Support\MPLog-[date]-[time].log
I hope the above information helps. Let’s know your comments.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!
