Windows 10 and 11 include a beneficial security feature named Controlled folder access, which is part of the Microsoft Defender Exploit Guard. You may have noticed the Unauthorized changes blocked notifications. Microsoft Defender’s Controlled folder access feature is the one behind those notifications. Controlled folder access helps you protect valuable data from malicious programs, such as ransomware.
This article explains how to configure CFA and prevent Unauthorized changes blocked notifications when running a program.
Microsoft Defender Exploit Guard is a new set of host intrusion prevention capabilities for Windows 10/11, allowing you to manage and reduce the attack surface of apps installed on the computer.
Contents
What is Controlled folder access in Windows
 Controlled folder access is an anti-ransomware feature in Windows that helps protect your documents, files and memory areas on your computer from modification by suspicious or malicious apps (especially ransomware). Controlled folder access is supported on Windows Server 2019 as well as Windows 10/11.
Controlled folder access is an anti-ransomware feature in Windows that helps protect your documents, files and memory areas on your computer from modification by suspicious or malicious apps (especially ransomware). Controlled folder access is supported on Windows Server 2019 as well as Windows 10/11.
Sometimes Controlled folder access can block legitimate apps from writing to protected folders (such as the Desktop, Documents folders etc), and shows the notification Unauthorized changes blocked. You an configure Controlled folder access so that you can allow specific applications, as well as add custom folders to the list of “protected” folders.
It is especially useful in helping to protect your documents and information from ransomware that can attempt to encrypt your files and hold them hostage.
How to Use Controlled folder access?
Prerequisite: Microsoft Defender Antivirus real-time protection must be enabled for the Controlled folder access feature to work.
Enabling Controlled folder access
To enable Controlled folder access, use these steps:
- Double-click the Defender shield icon in the notification area to open the Microsoft Defender Security Center.
- Click Virus & threat protection
- Click Virus & threat protection settings
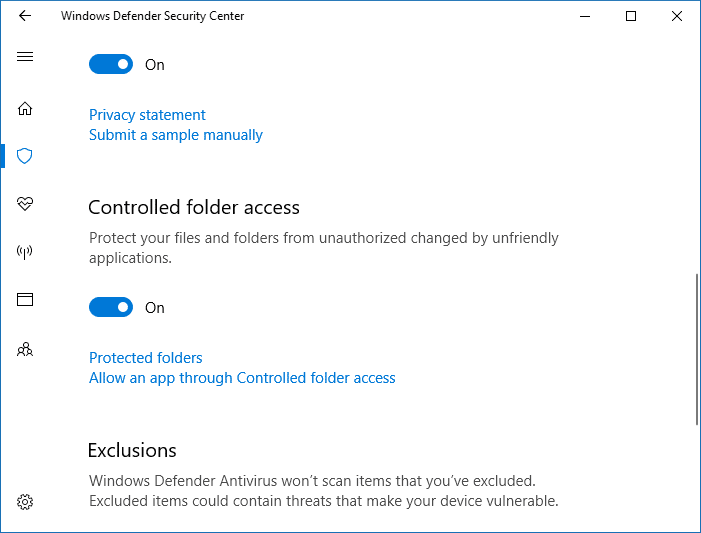
Enabling Microsoft Defender Controlled folder access - Enable the “Controlled folder access” setting. UAC dialog will pop up now for getting your confirmation/consent.
From now on, Controlled folder access monitors the changes that apps make to files in the protected folders.
Enable protection for additional folder locations
By default, these folders are protected, and there is no way to remove protection for these folders:
User shell folders: Documents, Pictures, Videos, Music, Favorites, and Desktop Public shell folders: Documents, Pictures, Videos, and Desktop
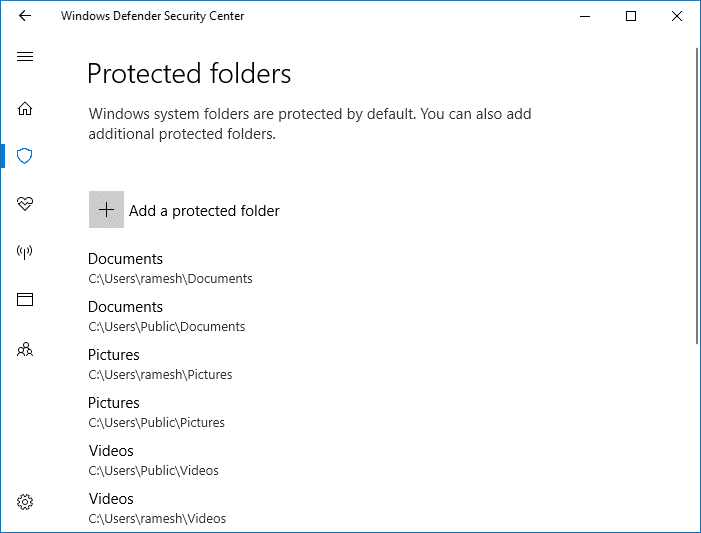
However, some users may not prefer storing their files in the personal shell folders or libraries; they may have their documents in a network share or other locations. In that case, you can bring additional folder locations under Microsoft Defender protection, by clicking Protected folders link in Microsoft Defender Security Center, and clicking Add a protected folder button. You can also enter network shares and mapped drives.
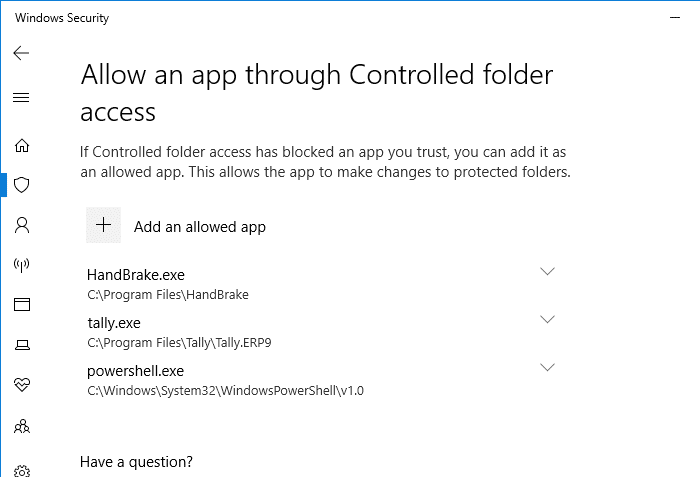
Add (whitelist) apps for Controlled folder access
Microsoft Defender Controlled folder access will block write access (by “unfriendly” apps) to files in protected folders. If an app attempts to make a change to these files, and the app is blacklisted by the feature, you’ll get a notification about the attempt.
Just as you can complement the protected folders with additional folder paths, you can also add (whitelist) the apps that you want to allow access to those folders.
Notepad++ blocked
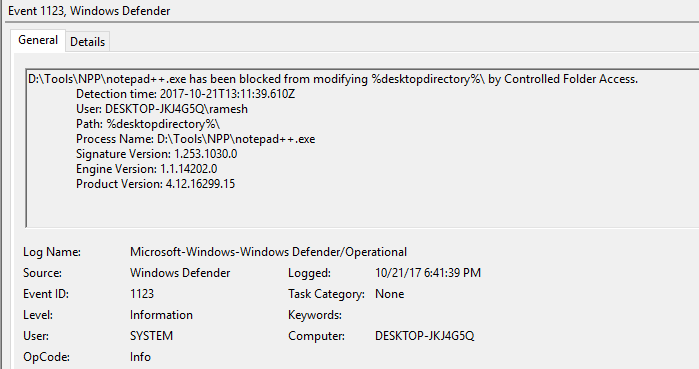
In my case, Controlled folder access was blocking the 3rd party text editor program Notepad++ from saving to the desktop.
And an event log entry (Event ID: 1123) is generated for the blocked event.
It will be listed under Applications and Services Logs → Microsoft → Windows → Windows Defender → Operational
| Event ID | Description |
|---|---|
| 5007 | Event when settings are changed |
| 1124 | Audited Controlled folder access event |
| 1123 | Blocked Controlled folder access event |
| 1127 | Blocked “changes to the memory” event? |
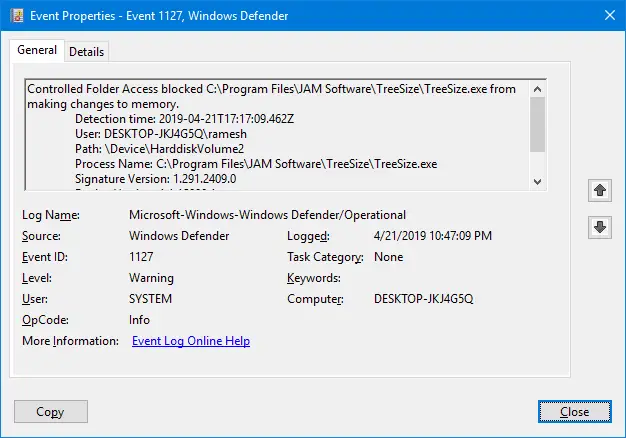
There is no official info regarding CFA Event ID: 1127. It could be related to blocked “making changes to memory” events. I found an interesting entry in my system.
Log Name: Microsoft-Windows-Windows Defender/Operational
Source: Microsoft-Windows-Windows Defender
Date:
Event ID: 1127
Task Category: None
Level: Warning
Keywords:
User: SYSTEM
Computer: DESKTOP-JKJ4G5Q
Description:
Controlled Folder Access blocked C:\Program Files\JAM Software\TreeSize\TreeSize.exe from making changes to memory.
Detection time: 2019-04-21T17:17:09.462Z
User: DESKTOP-JKJ4G5Q\ramesh
Path: \Device\HarddiskVolume2
Process Name: C:\Program Files\JAM Software\TreeSize\TreeSize.exe
Signature Version: 1.291.2409.0
Engine Version: 1.1.15800.1
Product Version: 4.18.1903.4
To get the list of the last 25 blocked apps, open a Command Prompt window and run this command-line:
wevtutil qe "Microsoft-Windows-Windows Defender/Operational" /q:"*[System[(EventID=1123)]]" /c:15 /f:text /rd:true | findstr /i "process name:"
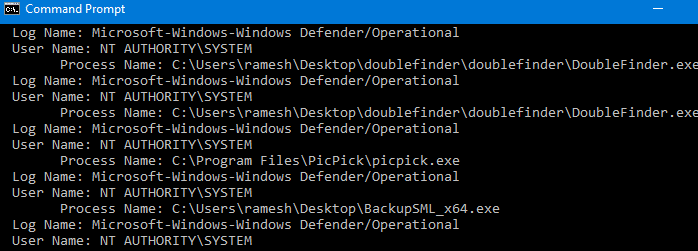
Also, see the PowerShell script at the end of this article to list items in a listview grid window and whitelist selected items in a single click.
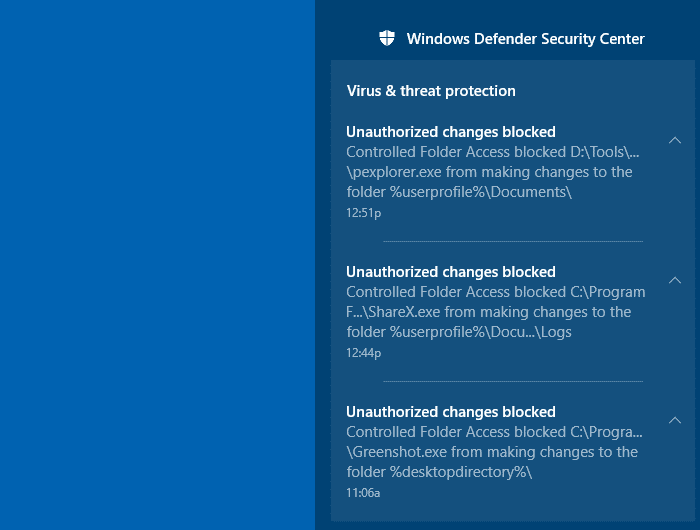
Here is the list of Unauthorized changes blocked notifications, as seen in the Action Center.
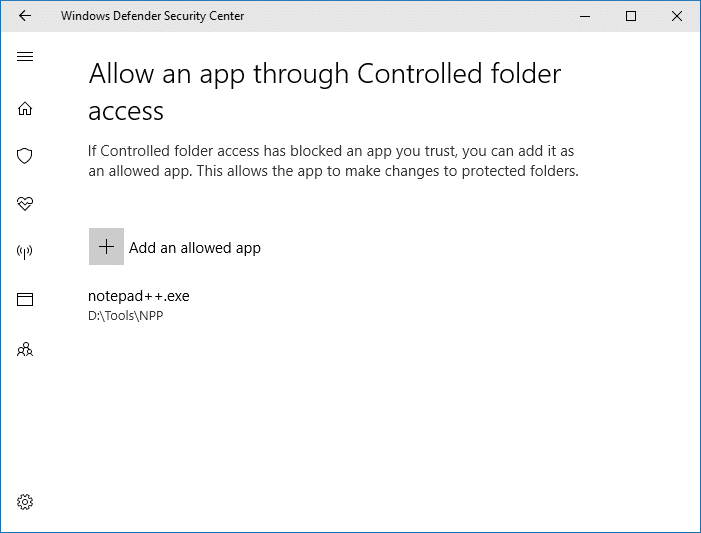
I allowed the app right away, as Notepad++ is a widely used and trusted program. To allow an app, click Allow an app through Controlled folder access option in Microsoft Defender Security Center. Then, locate and add the app you want to allow.
Allow recently blocked apps
The Controlled folder access also lets you allow apps that were recently blocked. To see the list of apps that are blocked, click on the Add an allowed app button, and click Recently blocked apps.
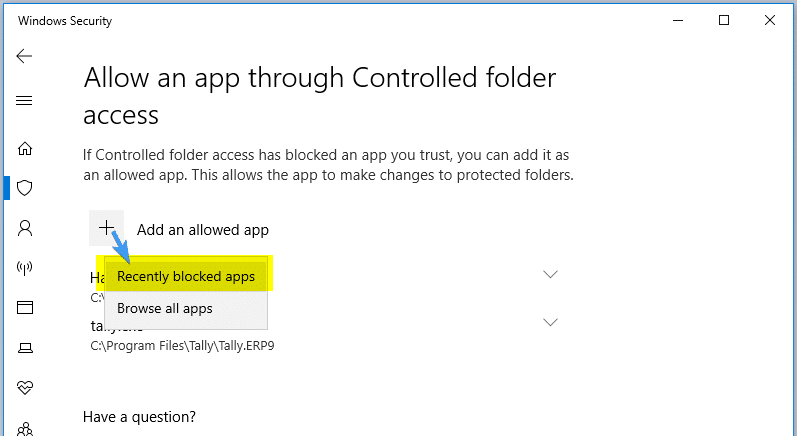
You’ll get the list of apps there were recently blocked. From the list, you can click select an app and add it to the allow list. To do so, you need to click on the + glyph icon or button near the app entry.
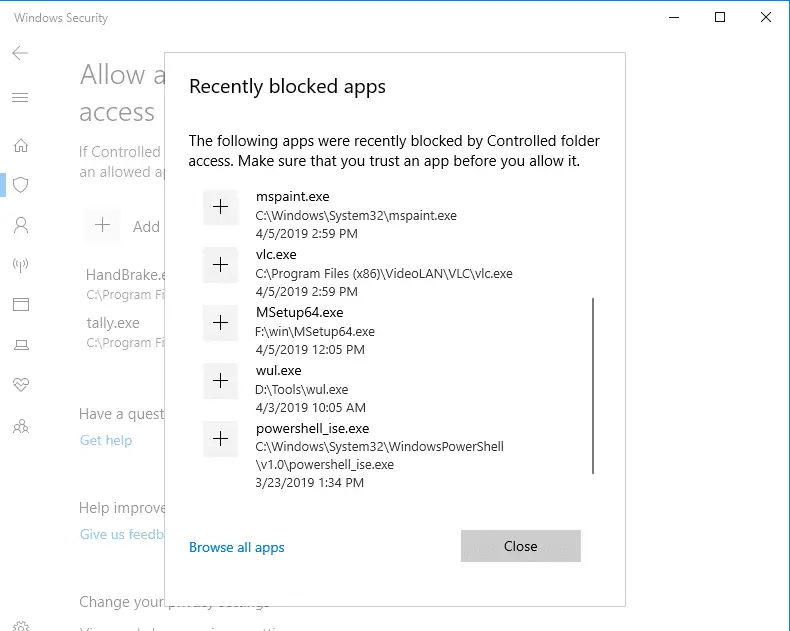
Here, I’ve whitelisted PowerShell.exe process, as an example.
Make sure you allow only the apps you trust. Allowing PowerShell.exe should be done with extreme caution, as crypto-malware may silently execute a PowerShell command or script on a vulnerable computer.
Manage Controlled folder access Using PowerShell
PowerShell’s Set-MpPreference cmdlet supports many parameters so that you can apply every Microsoft Defender setting through script. For the full list of parameters supported by this cmdlet, check out this Microsoft page.
Enable Controlled folder access using PowerShell
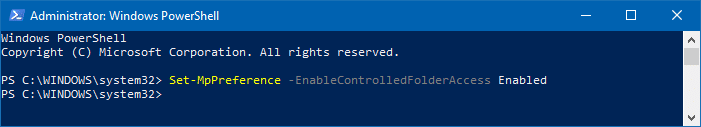
Start powershell.exe as administrator. To do so, type powershell in the Start menu, right click Windows PowerShell and click Run as administrator.
Enter the following cmdlet:
Set-MpPreference -EnableControlledFolderAccess Enabled
To disable, use this command:
Set-MpPreference -EnableControlledFolderAccess Disabled
Protect additional folders using PowerShell
Add-MpPreference -ControlledFolderAccessProtectedFolders "c:\apps"
Allow a specific app (Notepad++) using PowerShell
Add-MpPreference -ControlledFolderAccessAllowedApplications "d:\tools\npp\notepad++.exe"
Allow all blocked apps to Controlled folder access (interactively) using PowerShell
Redditor /u/gschizas has come up with a neat little PowerShell script which parses the event log (entries with ID: 1123 which is the “Blocked Controlled folder access” event) to gather the list of apps blocked by Microsoft Defender’s Controlled folder access. The script then offers to whitelist all or selected programs from the listing.
How to use the script?
- Open PowerShell as administrator.
- Visit the gschizas GitHub page
- Select all the lines of code and copy to clipboard.
- Switch to the PowerShell window and paste the contents there, and press ENTER
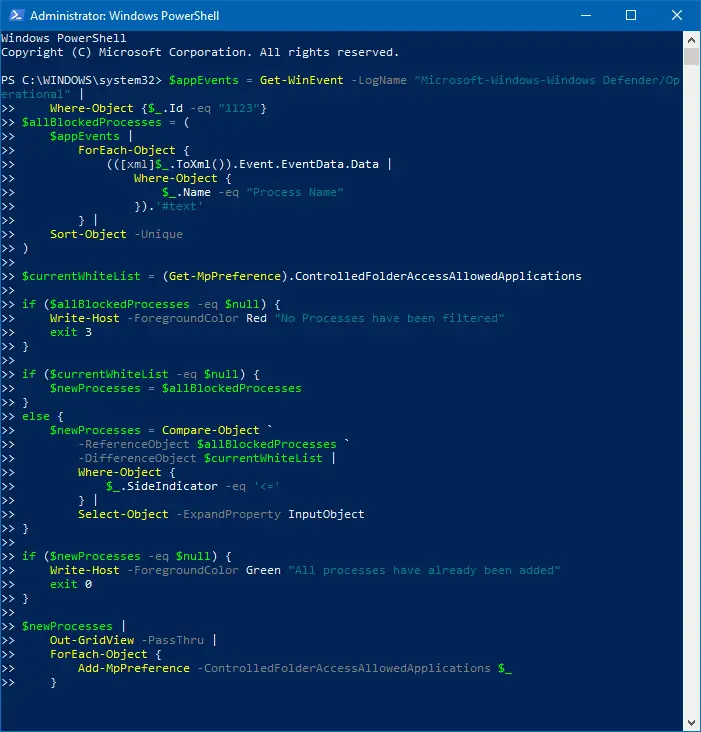
Allow all apps through Controlled folder apps –Powershell script The list of blocked apps is shown, as recorded in the event log.
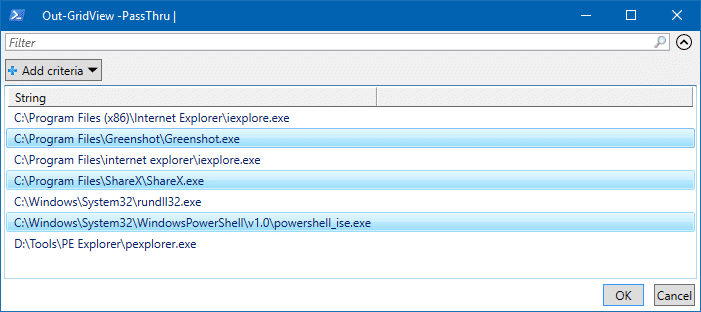
Select the apps to whitelist - Select the apps you want to whitelist and click OK. To multi-select programs, press the Ctrl button and click on the corresponding entry.
- Click OK.This allows the apps through Controlled folder access en masse.
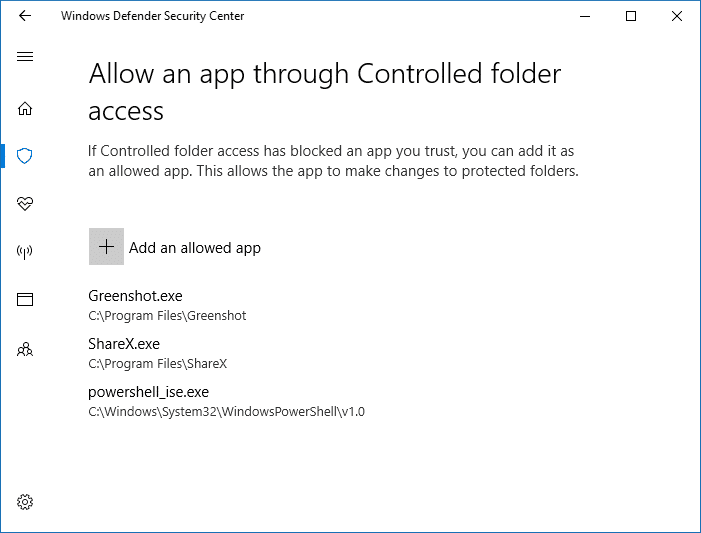
Apps added to Controlled folder apps “Allow” list
In an enterprise environment, Controlled folder access can be managed using:
- 1. Windows Defender Security Center app
- 2. Group Policy
- 3. PowerShell
Troubleshooting: Controlled folder access option missing, grayed out or inaccessible
When you try to open the Controlled folder access page via Start, you may see this error message:
Page not available
Your IT administrator has limited access to some areas of this app, and the item you tried to access is not available. Contact IT helpdesk for more information.
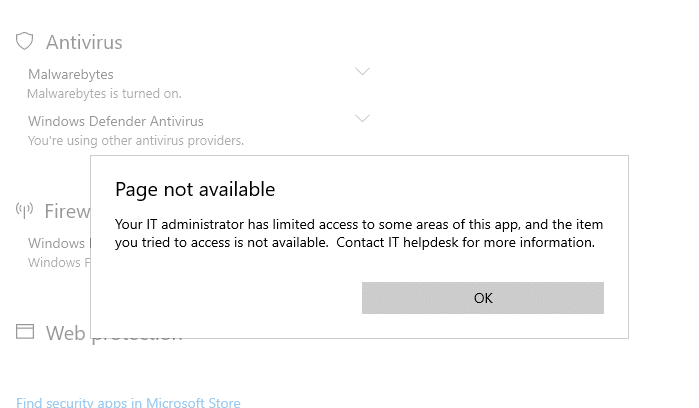
You may be wondering if the above error is caused by some group policy restrictions in effect on your computer. It may not necessarily be true.
The error occurs if you’re using a third-party antivirus solution on your computer, which would have turned off the built-in Microsoft Defender. As stated earlier, the Controlled folder access feature fully relies on Microsoft Defender real-time protection. If Microsoft Defender is turned off, Controlled folder access wouldn’t work. Hence the page remains inaccessible or grayed out, depending upon the build of Windows 10/11 you’re using.
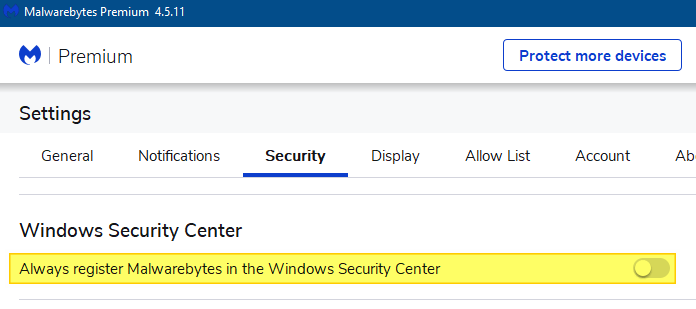
In my case, the error occurred after I installed Malwarebytes Premium. It had replaced Microsoft Defender.
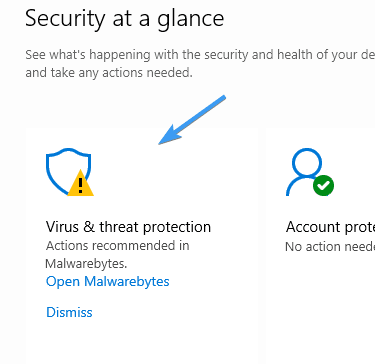
Note: If you’re a Malwarebytes premium user, you can still enable and use Defender alongside Malwarebytes premium.
To do so, open Malwarebytes Premium → Settings → Security → Disable Always register Malwarebytes in the Windows Security Center.
This option ensures that Malwarebytes Premium doesn’t turn off Microsoft Defender Antivirus. It can run alongside Defender so that the Controlled folder access feature would work as well. After turning off the setting, the Malwarebytes program status wouldn’t appear in the Windows Security Center.
Enable or disable Controlled folder access using desktop shortcuts
In some situations, you may need to temporarily disable Controlled Folder Access to allow programs to write to protected folders, without having to whitelist each program. For example, you may have whitelisted the ShareX program, but screen captures may still not work because the video capture and processing tool FFMpeg.exe is not whitelisted in Controlled Folder Access. And you may not want to allow the external program permanently.
For this purpose, you can create two desktop shortcuts to disable/enable Controlled Folder Access quickly.
- Right-click on the desktop, click New, shortcut
- In the “Type the location of the item” text box, type the following command:
powershell.exe -command "& {Set-MpPreference -EnableControlledFolderAccess Enabled}"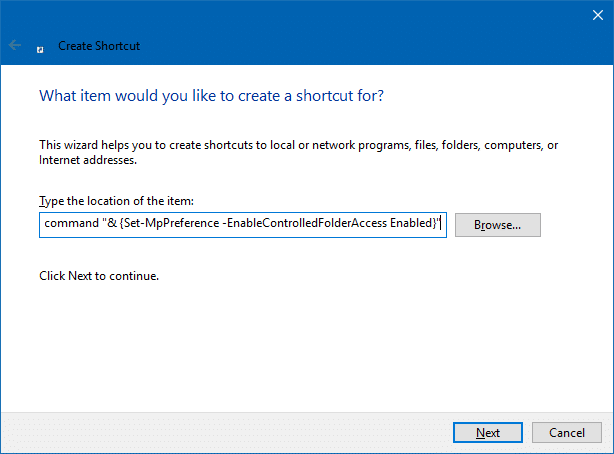
- Name the shortcut “Enable Controlled Folder Access”.Quick Tip: In the shortcut Properties tab, you may configure it to run minimized if you don’t want to see the PowerShell window when the command is executed. Of course, PowerShell.exe need to be whitelisted in order for these shortcuts to work. PowerShell’s executable path is
C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exeif you’re going to whitelist it. - Similarly, create another shortcut with the following target:
powershell.exe -command "& {Set-MpPreference -EnableControlledFolderAccess Disabled}"Name it as “Disable Controlled Folder Access”, and optionally, change the shortcut icon for both the items as desired.
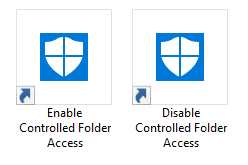
Run as Administrator
The shortcut/command has to be run elevated (as administrator). So, right-click each shortcut and click Properties. Click Advanced, and enable “Run as Administrator” checkbox, and click OK, OK.
Repeat the step for the other shortcut.
Closing words
Microsoft Defender Antivirus is getting a new security feature in almost every Windows 10 build. To name a few, Microsoft Defender Offline scanner, Limited Periodic Scanning, “Block at first sight” Cloud-protection and Automatic sample submission, and adware or PUA/PUP protection capability, and Application Guard.
And now Controlled folder access introduced in the Fall Creators Update is yet another valuable feature to guard the system against threats, such as ransomware.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!
Tried it out but quickly turned it off. It was blocking explorer.exe and all Microsoft Office programs by default. You’d think Microsoft would know to whitelist their own programs. Guess not.
Matthew: That’s strange. Explorer.exe isn’t be blocked in my systems. Haven’t tried Office though.
I found the same thing. First, it blocked a third-party app, which is well-known. I scanned it; it was clean; I put it on the trusted app list. But then, within an hour, it blocked me from saving a Microsoft Word file. I turned Controlled Access Folder off. I am done with it for now. I run premium Malwarebytes for anti-ransomware protection.
nice!!! somebody with a real, straightforward answer rather than the useless!ss drivel that comes from the usual micosoft community!
Great, this will work a treat.
Wondering if there’s a way to open CFA as admin so that you can add/remove apps without having to admin elevate each one.
thx very helpful article. particularly the script!
How helpful! CFA is a great idea, but it’s a hassle weeding through Windows Defender’s settings pages to get to it each time we want to install something legitimate that modifies a protected folder. Thanks for sharing this excellent tip.
To make the Disable shortcut work, you must also add Power Shell to the list of apps CFA allows. It’s rather a Catch-22 otherwise. ;?)
I seriously hate this controlled folder access; it started blocking every app I’ve used until now and because of it I have had to reinstall and redownload it is so freaking annoying. This update is not an improvement.
As far as I can see control folder access is a great idea BUT as is often the case the designers have never used it as part of their PC Setup!!!!!
As it stands I suggest it is unusable especially by the average non technical PCUser
When a conflict is detected the User should be prompted by a MSG BOX and given the choice of rejecting the call or adding the program the the accepted list.
It is almost there clicking on the Action LIst entry displays the “allow the app controlled folder access” if the path of the program was displayed with the option to add it the system would be part way usable. (“prompts for admin password”)
A great tip… thanks a lot.
You could edit the post, though, to include Ander’s advice that you must also add Power Shell to the list of apps CFA allows for it to work…
Cheers.
It is blocking my downloaded open office and I cannot get it to save. It didn’t do it on my last PC.
I am not competent to go into the shell.!!!
Kris It (CFA) was not enabled by default, it seems your enabled it from settings and forgot it. This is just quick way to enable or disable that settings.
It has done nothing but make my pc run terrible I wish there I can figure out how to turn it off!!!!!!!!
Where is the powershell app to add to the allowed CFA? I can’t find it on the C: drive under Windows…
So how do you add Power Shell to approved programs? Iv’e never heard of this CFA until now.
Thanks alot. I have to thank yourself for writing a very legible document explaining the complex nature of controlled folder access. I usually have great difficulty understanding technical writings because largely they are poorly described not this one it is very well done. I am not usually so generous with compliments concerning computers and their operations so thanks again. bernard.
Unable to install Iolo Phoenix 360 due to this “feature”. Will try whitelisting, but if that doesn’t work, I’ll just turn the feature off. What a pain! Iolo Cust. srvc. didn’t think of this one. Thanks for article.
PowerShell.exe is located at:
%SystemRoot%\system32\WindowsPowerShell\v1.0\powershell.exe
As soon as you install an application you need to whitelist the process in CFA. After installing Notepad++ and LibreOffice I had to allow the following processes:
C:\Program Files\LibreOffice\program\soffice.bin
C:\Program Files\Notepad++\notepad++.exe
This article helped me. Thank you!
This needs to be updated as to how MS has at last provided an easy means to add an app from the list of “blocked apps”. Is now “almost” user friendly!
Interesting, Notepad++ is signed, so it shouldn’t have been blocked. But maybe this article is a little old now.
hey i have this problem with controlled folder access thing. If i turn on this setting, i can’t delete/rename/move eveything on documents and else, it said that i need permission from the administator, meanwhile i’m the administrator. but if i turn off, the controlled folder access, i can rename, move and delete everything in my folder. can someone help me with this issue?
I’ve got wmplayer.exe (both 32 and 64-bit) added to the allowed list, yet I keep getting the “unauthorized changes blocked” message, at least every 15 minutes for WMP and my Music directory. When I click on the message in the block history, it no longer gives me the option of allowing the app to access the Music folder, I suppose because it’s already on the allowed list. This has been going on for several days, since I applied the last Windows security update. Funny thing is that I don’t use WMP on this computer, and I have nothing stored in the Music directory.
@Reagan: When the message appears the next time, use wevtutil command or PowerShell (as mentioned in the article) to find out which executable is being blocked, exactly.
Greetings from Portugal, is there a way to clear the historical from the applications Controlled Folder Access.
Cleaning the WD history is by deleting the “store” folder in C:\ProgramData\Microsoft\Windows Defender\Scans\History\Store but it does not clear the historical off “blocked applications.”
Thanks in advance.
I can’t even access Controlled Folder Access. Standalone PC, not corporate or administered by anyone but me. I get a message
Page not available
Your IT administrator has limited access to some areas of this app, and the item you tried to access is not available. Contact IT helpdesk for more information.
I AM MY IT HELPDESK.
@AD: See if some Windows Defender policies are enabled accidentally. Ref: https://www.winhelponline.com/blog/windows-defender-disabled-real-time-protection-virus/
I also made a shortcut to the controlled folder access page using this as the location for a new shortcut:
windowsdefender://ProtectedFolders/