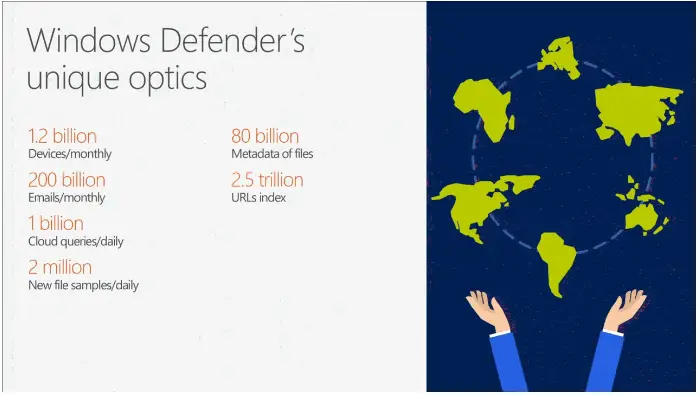
Windows Defender or the Microsoft anti-malware platform protects home computers, servers and online services such as Office 365. With the wealth of threat intelligence and telemetry data, Defender’s cloud backend is an astounding malware protection service.
When a new malware appears in the wild, it can take hours for the Microsoft anti-malware team (or any other anti-virus or anti-malware company for that matter) to analyze, reverse engineer and perform malware detonation of the file before it can release a signature update. And, not to mention the QC the signature update has to pass through.
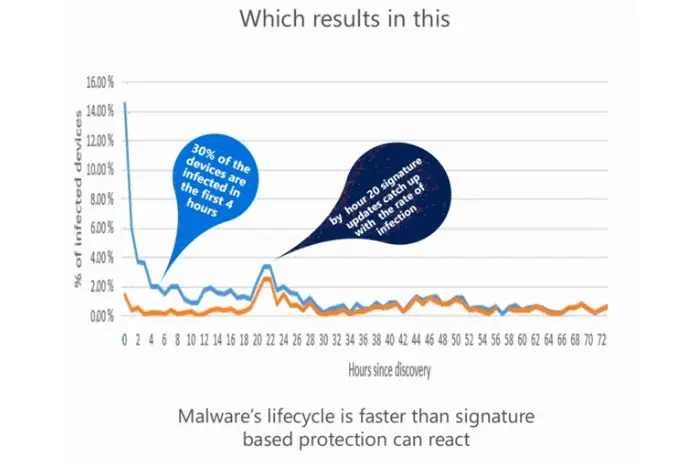
As far as malware protection is concerned, there is no denying the fact that signature-based protection is prime. But that’s not sufficient, as it may not always help — especially in the case of brand new or unknown malware. As per Microsoft’s report when a new malware appears, 30% of the computers are infected within the first four hours. The signature updates usually come hours later.
Windows Defender’s robust cloud-based protection, on the other hand, uses heuristics, machine learning model, and does detailed analysis at the backend to determine if a file is malware.
Windows Defender cloud-based protection or “block at first sight” feature is by default enabled. If you’ve turned off cloud protection option in Windows Defender due to “privacy” concerns, you better watch the demo by Windows Defender Engineering team, which shows how effective cloud protection can be.
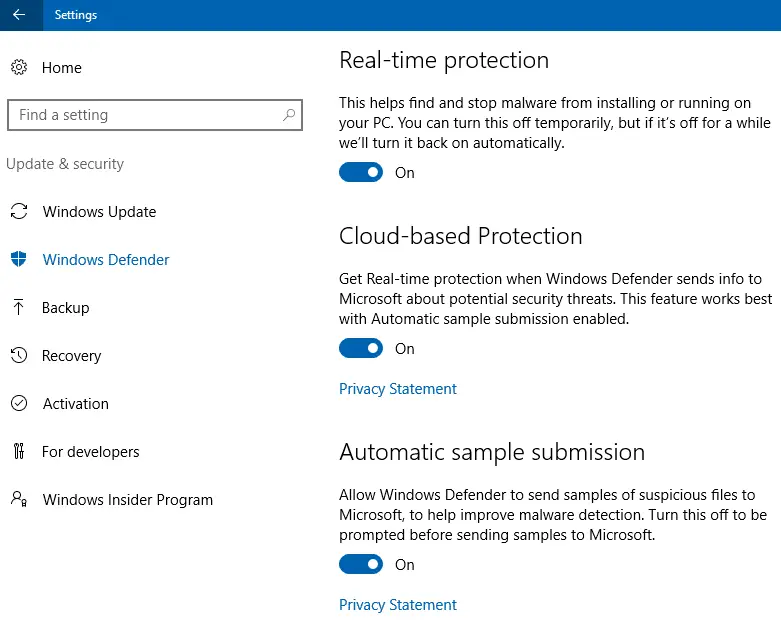
Make sure “Block at First Sight” Cloud Protection is enabled
Click Start, Settings. (Or press WinKey + i)
In the Settings page, click Update & Security and then Windows Defender.
Make sure that Cloud-based Protection and Automatic sample submission settings are enabled.
When Windows Defender’s “Block at first sight” cloud protection and sample submission options are enabled in Windows Defender Settings, if the system encounters a suspicious file which otherwise passes signature-based detection, Defender sends the metadata of the suspicious file to the cloud backend. Note that the cloud doesn’t always request the entire file.
The machines at the cloud backend analyze the metadata, making use of the various logics, URL reputation, and telemetry data to determine if the file is malware.
For example, if the malware filename matches the name of a core Windows module, the cloud backend checks the digital signature of the module. If it’s unsigned or not signed by Microsoft, and it’s “classification” is malware (with “confidence” level 85%), then the cloud determines the file is malware.
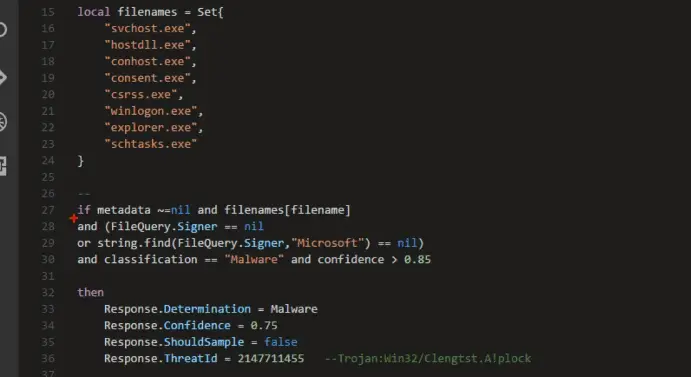
The “Classification” and “confidence” assessments which constitute the most important part of the backend analysis, are obtained through the machine-learning model.
In case the cloud backend comes up with no verdict, it requests the entire file for a detailed analysis. Until the file is uploaded and the cloud confirms the receipt of the same, Windows Defender locks the file and doesn’t allow to run on the client. That’s a key change the Windows Defender team has made in the Windows 10 Anniversary Update (v1607).
Previously, the suspicious file was allowed to run while the upload was in progress, synchronously. Even before the upload completed, the malware would have finished running and self-destroyed itself.
Coming to Windows Defender Engineering team’s demo, there were two scenarios discussed. In Scenario 1, the cloud backend classifies a file as malware, only based on the metadata. Device #1 with cloud protection turned off, gets infected when running the file. And device #2 with cloud protection On, is instantly protected.
In Scenario 2, the first user runs an unknown malware. The cloud reached no verdict based on the metadata, and thus the entire file was automatically submitted.
The submission time was at 19:48:59 hours – backend completed the automated analysis at 19:49:01 hours (~2 seconds from the time upload hit the cloud backend) and determined the file is malware.
From the very moment, Windows Defender would block any future encounters of that file, thus protecting millions of other devices which have Windows Defender cloud-based protection enabled.
Microsoft also has a test site named Windows Defender Testground where you can check the effectiveness of Defender’s cloud protection by uploading samples.
Although the second demo didn’t succeed due to some connectivity issues with the cloud, overall it’s a useful presentation which explains the importance of Windows Defender’s “block at first sight” cloud-based protection feature. If you had turned off the feature, I guess you’ll now have a second thought.
References & Credits
Enable the Block at First Sight feature to detect malware within seconds
Explore Windows Defender Instant Protection | Microsoft Ignite 2016 | Channel 9
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!