When you download a file you downloaded from the internet, Windows adds the zone identifier or Mark of the Web as NTFS stream to the file. So, when you run the file, Windows SmartScreen checks if there is a zone identifier alternate data stream attached to the file. If the ZoneId=3 data ADS is present, Windows identifies that the file was downloaded from the internet, and the SmartScreen does a reputation check when you run the file.
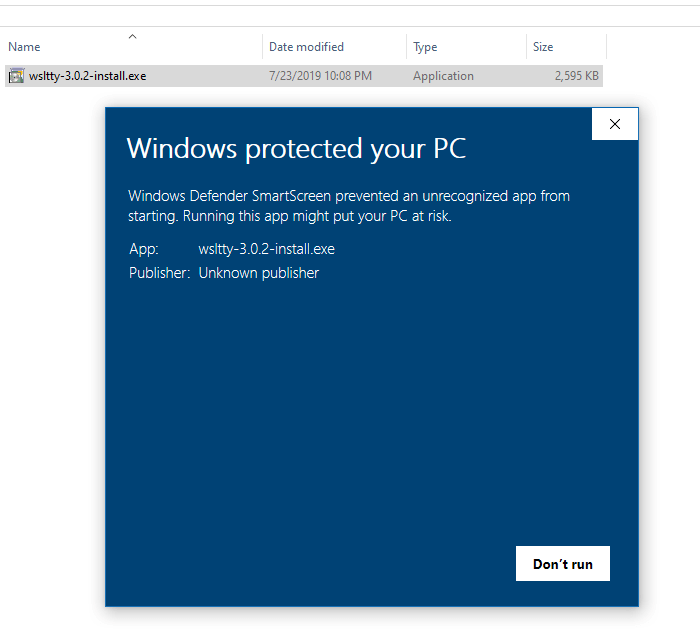
If the file has a bad reputation according to the Microsoft SmartScreen server, you’re adviced not to run the file, with an option to run the file anyway despite the warning. The warning reads Windows protected your PC. Windows SmartScreen prevented an unrecognized app from starting. Running this app might put your PC at risk.
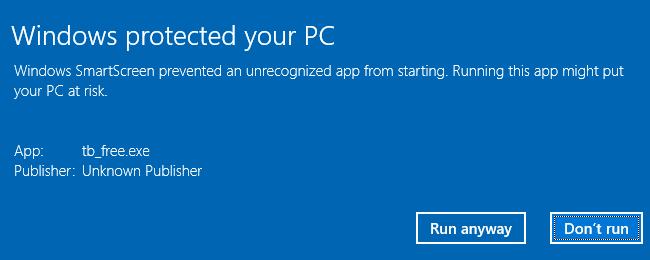
Zone ID 3 represents the “Internet Zone”. If you downloaded the file using Chrome or Chrome-based browsers, you’ll also see the ReferrerUrl and HostUrl data in the NTFS stream.
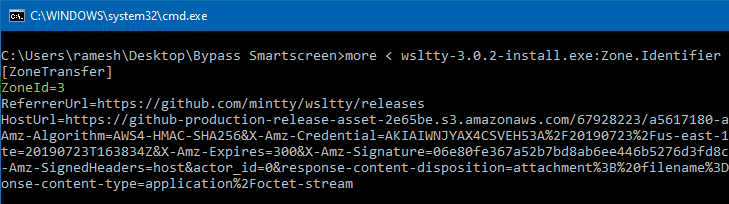
To prevent the SmartScreen, you usually right-click on the file, click Properties, select the Unblock checkbox and click OK.
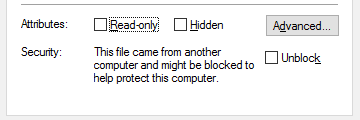
But if you have the Hide mechanisms to remove zone information policy located under the node User Configuration → Windows Components → Attachment Manager in the Group Policy Editor enforced, the Unblock option would be missing in the file’s properties tab.
Also, the SmartScreen group policy can be configured such that you don’t get the Run anyway option, and the users can’t turn off SmartScreen via Windows 10 Settings UI.
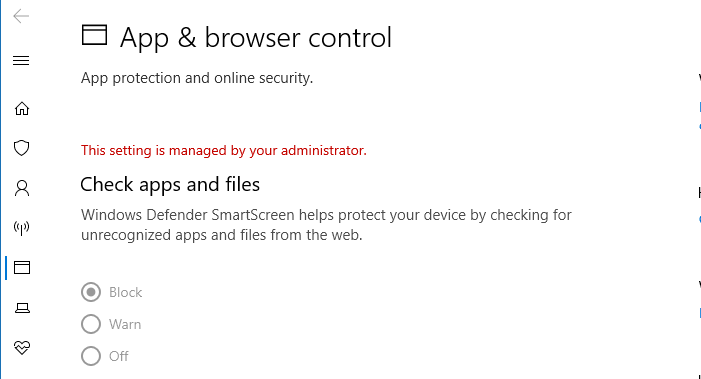
The relevant policy setting is Configure Windows Defender SmartScreen under Computer Configuration → Windows Components → File Explorer.
Setting it to Warn and prevent bypass removes the Run anyway option.
The corresponding registry settings for the above two Policies are below:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments Value: HideZoneInfoOnProperties Type: REG_DWORD, Data: 1 HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System Value: EnableSmartScreen Type: REG_DWORD, Data: 1 HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System Value: ShellSmartScreenLevel Type: REG_SZ, Data: Block
Bypass SmartScreen even if it is Enabled through Group Policy
However, even with the above policies configured, there is a loophole method to bypass SmartScreen using a registry value which can be configured per-user — i.e., under HKEY_CURRENT_USER.
Let’s say you get this screen when running a downloaded installer in your Windows 10 computer.
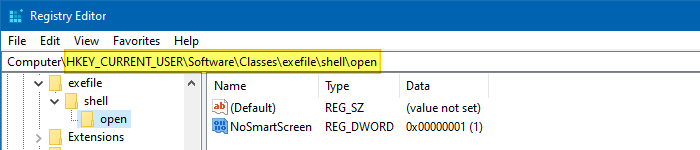
To bypass the SmartScreen, create a DWORD (32-bit) value named NoSmartScreen under the following registry key:
HKEY_CURRENT_USER\Software\Classes\exefile\shell\open
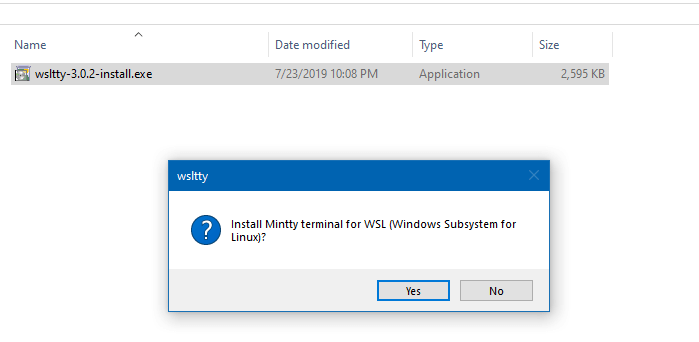
Now, the file runs without going through the SmartScreen check!
Another way to prevent the SmartScreen is to remove the zone information using PowerShell (as the Unblock option in file properties is now hidden using Policy). If the user has access to PowerShell, he can run the Unblock-file cmdlet to easily remove the zone identifier information from the file.
The above bypass works only if the user is able to create the NoSmartScreen registry value using one of the methods, such as Registry Editor, PowerShell, console reg.exe tool, WScript.exe, CScript.exe, or any other tool already present in the computer.
The SmartScreen is an extra layer of defense which can be useful in addition to your Windows Defender real-time and cloud protection features. Microsoft should ensure that the above loophole is plugged in the future Windows releases.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!
Hi, I have a question. How do I change zone information.